Gotta Catch'em All Writeup
Introduction
This is an easy challenge box on TryHackMe.
This is what a hint will look like!
Enumeration
Ports
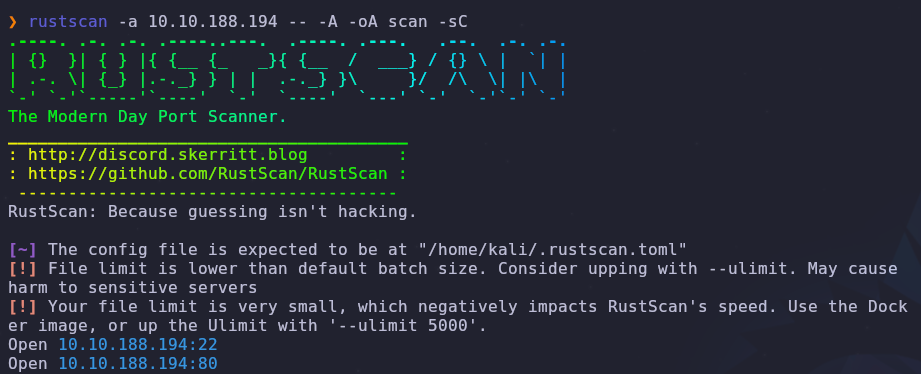
Let’s start with a port scan to see open ports and services
1
rustscan -a VICTIM_IP -- -A -os scan -sC
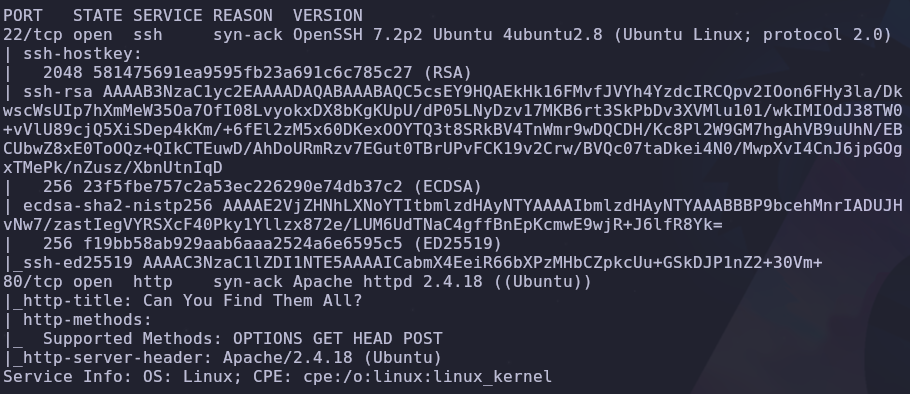
We have two open ports
- 22: SSH
- 80: HTTP
Web Server
View the homepage source and find credentials
Let’s visit the web server on port 80 and see what we can find
Looks like it’s running an Apache webserver. We can run subdirectory bruteforcing to find hidden files on the server but our foothold into the server is already present! Next we should check the source of the homepage
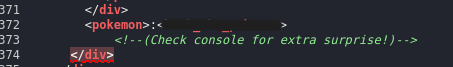
A colon is usualy used to separate a username from a password. By ignoring the tags we have a potential username and password!
We can also check what’s printed in the console
Cute it’s a list of gen 1 pokemon. There isn’t anything else to find here so don’t get too distracted
Initial Foothold
Use the credentials to
sshinto the server
Grass Type Flag
Search
pokemon’s home directory
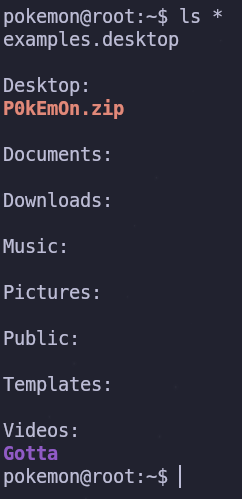
There are a few folders in pokemon’s home directory. We can check the first level of all of these folders using ls and a wildcard
1
ls *
The Desktop directory has an interesting zip file, so let’s check its contents
1
2
cd ~/Desktop
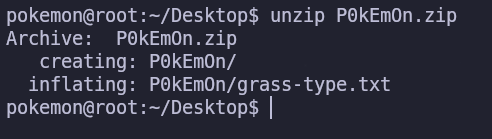
unzip P0kEm0n.zip
It has the grass type flag! We can read a file’s content with the cat command
1
2
cd P0kEm0n
cat grass-type.txt
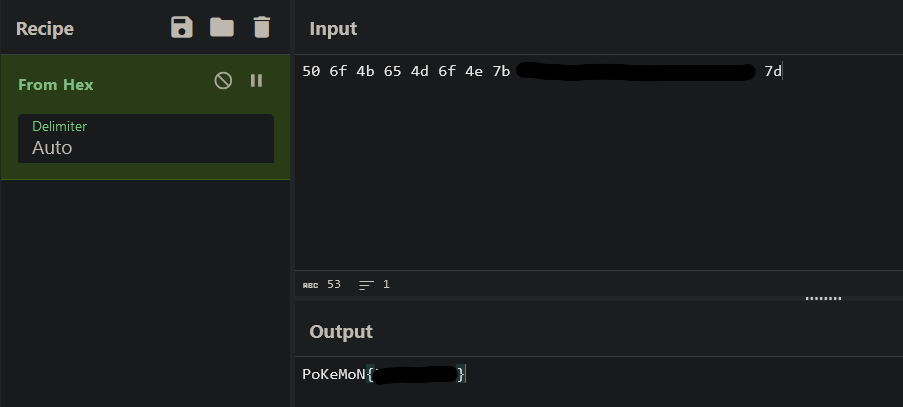
Seems like the flag has been encoded into hex. We can decode this (and the other flags) with cyberchef
Water Type Flag
Where are the web server files located?
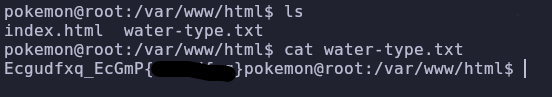
Next we should check the web server files. This is usually located in /var/www/html so let’s see if there is anything interesting
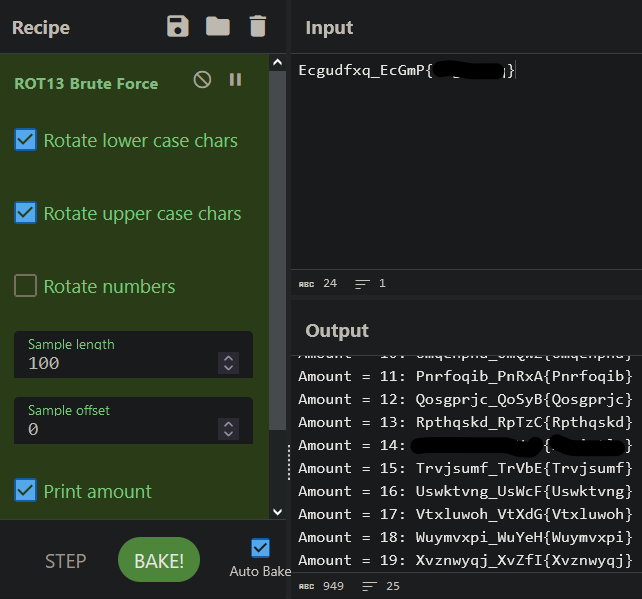
It’s the water type flag! It’s encoded again so let’s use cyberchef with the ROT 13 Brute Force option
Two flags down, two more to go
Horizontal Escalation
Check all the folders in
pokemon’s home directory
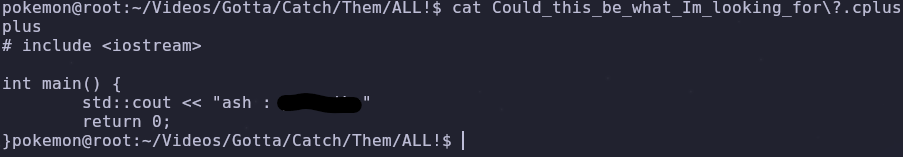
When we first checked pokemon’s home directory there was another folder in the Videos directory
Let’s traverse this directory to the bottom and read any files we find
The colon makes a comeback and it gives us credentials for the ash user! We can switch users with the command
1
su ash
Root
What
sudoprivileges does our new user have?
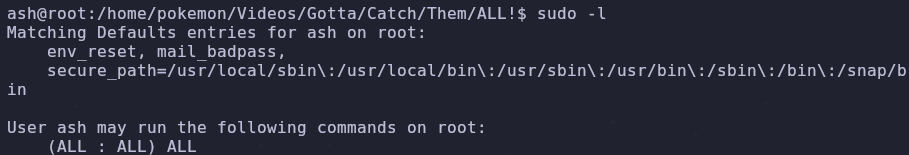
Now that we’re a new user we should see what privileges we have. We can check if we can run any sudo commands by using the -l flag
1
sudo -l
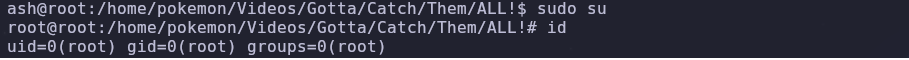
We have full sudo permissions! We can escalate to root by running su with sudo
1
sudo su
We can access everything on the server now so let’s start looking for flags
Fire Type Flag
Search the server for a flag with the
findcommand
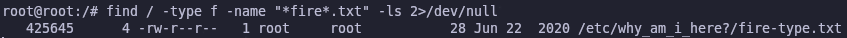
Since we don’t know where the flag is located we can use the find command which can search for the name of a file in a directory. By specifying the / directory we can search the entire server and we’re looking for a txt file with fire in its name
1
find / -type f -name "*fire*.txt" -ls 2>/dev/null
We found it! Let’s read it with cat
Now let’s decode it with cyberchef and the Base64 option
Root Flag
Check the
/homedirectory
The root flag is usually in /root/root.txt but it isn’t there! We can check the directories of other users in /home but by checking this directory we immediately find the flag
Conclusion
By investigating the source of the web server’s homepage we were able to find ssh credentials to gain a foothold into the system. Enumerating common directories lead us to the first two flags. They were in a zip file and the web server’s default directory. Further enumeration gave us the credentials of the ash user. By checking ash’s sudo permissions we were able to escalate our privileges to root. Using find and investigating the /home directory we were able to obtain the final two flags.